Understanding TPRM Compliance: A Comprehensive Guide

In any industry, adherence to regulatory compliance and reporting is integral to daily operations and ensuring business resilience. As vendors and suppliers are increasingly associated with data breaches and supply chain disruptions, many organizations are now obligated by industry and government regulations to extend their compliance efforts to ensure proper third-party governance as well. This requires establishing a robust third-party risk management program.
In this comprehensive guide, we will explore the key aspects of TPRM compliance, emphasizing its significance, the role of risk assessments, continuous monitoring, cybersecurity frameworks, ESG regulations, industry guidelines, data privacy regulations, and practical steps for your organization to start its TPRM compliance journey.
Understanding TPRM Compliance
TPRM is the linchpin for organizations navigating a labyrinth of regulations relating to their use of vendors and suppliers. Tackling compliance is a multifaceted challenge that necessitates a strategic approach.
TPRM Programs are Essential to Meet Compliance Regulations
To comply with various regulations, guidelines, and standards, your organization should adopt a third-party risk management (TPRM) program. This includes a multi-step approach where you:
- Set the rules of third-party engagement based on your organization’s risk tolerance and data security and privacy policies
- Include these rules, as well as auditing requirements, in all third-party contracts
- Evaluate third parties via questionnaire-based risk assessments
- Measure performance against contractual agreements
- Continuously monitor third parties to verify compliance
- Remediate deficiencies
- Report to internal and external stakeholders
Utilize Frameworks to Set Up and Support Your TPRM Program
TPRM frameworks, such as the Standard Information Gathering (SIG) questionnaire and NIST 800-161 standard, offer a roadmap for building programs based on industry-standard best practices. Information security frameworks like NIST CSF, ISO 27001, and ISO 27036-2 supplement TPRM efforts. Leveraging TPRM frameworks ensures a comprehensive program that reduces risks for both the organization and its customers.
On-Demand Webinar: Keeping Up With Changing TPRM Compliance Frameworks
Compliance experts Alastair Parr and Thomas Humphreys provide their best practices for staying on top of the ever-evolving world of third-party risk management compliance frameworks.
The Role of Risk Assessments and Continuous Monitoring in TPRM Compliance
Regulations like HIPAA often hold organizations accountable for non-compliance by their vendors, necessitating thorough risk assessments to measure the effectiveness of vendor security and data privacy controls and policies. In addition to regular risk assessments, continuous third-party monitoring is crucial to providing ongoing visibility into vendor threats and addressing real-time cybersecurity, financial, ethical, reputational, and operational risks.
Third-party risk assessments are conducted throughout the vendor risk lifecycle to holistically assess the organizational risk posed by specific vendors and suppliers. Often, results are mapped to key requirements outlined in industry or regulatory frameworks such as ISO, HIPAA, PCI DSS, UK Modern Slavery Act, GDPR, NIST CSF, and others. In addition to regular risk assessments, continuous third-party monitoring is essential to maintain continuous TPRM compliance and best practices.
A lot can happen in the time between vendor risk assessments. That is why it is important to gain ongoing visibility into vendor threats. Actively monitoring third parties for cybersecurity, financial, ethical, reputational, and operational risk is critical to ensuring the ongoing stability and resilience of your organization's supply chain.
Organizations and stakeholders can achieve continuous insight into the compliance posture of vendor organizations by integrating deep security data collection and analysis with a third-party risk management approach, aiding in the defense of internal systems, conducting site visits, and reviewing records. Third-party monitoring ensures sustainability, trust, and transparency in vendor relationships.
Streamline TPRM Compliance with Automation
Ensuring internal adherence to regulations, guidance, and industry standards is complex and challenging at best (especially when you rely on spreadsheets). Tack on compliance mandates related to third parties, vendors, business associates, and supply chain partners, and the burden of managing risk takes an entirely new trajectory.
Prevalent offers a single, unified third-party risk management (TPRM) platform that streamlines your compliance initiatives by automating risk assessments, monitoring, analysis, and reporting throughout the vendor lifecycle.
Cybersecurity Frameworks
Cybersecurity frameworks play a crucial role in implementing and maintaining TPRM compliance. They help organizations adhere to guidelines, best practices, and standards for identifying, assessing, and managing third-party cybersecurity risks in a common language. By incorporating these frameworks in their TPRM compliance programs, organizations can effectively manage third-party risks, ensure regulatory compliance, protect sensitive data, and maintain stakeholders' trust.
Key Cybersecurity Frameworks
| Framework | Summary |
|---|---|
|
CAIQ provides a way to document security controls in cloud services, increasing transparency and assurance, and helping gauge the security posture of prospective cloud service vendors. |
|
|
These controls relate to Service Provider Management and Incident Response Management, respectively, and are integral to TPRM. |
|
|
CMMC compliance ensures that companies entering into contracts with the Department of Defense have adequate safeguards in place to protect non-public data. |
|
|
This order aims to modernize cybersecurity defenses by protecting Federal networks, improving information sharing, and strengthening the United States’ ability to respond to incidents. |
|
|
These standards provide a framework for establishing, implementing, maintaining, and improving an information security management system. |
|
|
This guidance helps organizations assess the cybersecurity of their supply chain. |
|
|
This framework provides guidelines and best practices to help organizations manage the risks associated with artificial intelligence (AI) systems. |
|
|
These standards provide a set of guidelines for federal information systems to ensure their security and privacy. |
|
|
This updated framework, provides enhanced cybersecurity supply chain risk management guidance. |
|
|
A standard used to ensure that companies have adequate safeguards in place to protect cardholder data. |
|
|
These rules require public companies to disclose cybersecurity risks and incidents, which includes risks associated with third parties. |
|
|
The SIG questionnaire is a tool used by organizations to assess and understand the IT, privacy, data security, ESG, and business resiliency risks posed by their third parties. |
|
|
SOC 2 reports provide detailed information and assurance about a service organization's security, availability, processing integrity, confidentiality, and privacy controls, including those related to third-party vendors. |
Navigate the TPRM Compliance Landscape
The Third-Party Risk Management Compliance Handbook reveals TPRM requirements in key regulations and industry frameworks, so you can achieve compliance while mitigating vendor risk.

ESG Regulations
In recent years, ESG (environmental, social, and governance) considerations have gained increasing importance, with governments now enacting legislation encompassing various aspects of ESG. This includes establishing mandatory reporting requirements and active measures to ensure corporations integrate ESG principles into their core decision-making processes.
ESG compliance requirements address operational risks impacting third parties and extended supply chains. Public companies carry a legal responsibility to assess the ESG practices of their third-party partners and extended supply chains, seeking information to evaluate risks associated with non-compliance with core ESG regulations. A well-designed third-party risk management (TPRM) program not only helps organizations meet current ESG requirements affecting supplier and vendor relationships but also positions them to align with future ESG regulations and standards.
Key ESG Regulations
| Regulation | Summary |
|---|---|
|
CTSCA (California Transparency in Supply Chains Act) |
The CTSCA requires certain companies to report on their specific actions to eradicate slavery and human trafficking throughout their supply chains. |
|
This act aims to foster sustainable and responsible corporate behavior by anchoring human rights and environmental considerations in companies’ operations, governance, and business relationships. |
|
|
The CSRD introduces more detailed sustainability reporting requirements for EU companies, non-EU companies meeting certain thresholds for net turnover in the EU, and companies with securities listed on a regulated EU market. |
|
|
The FCPA is a U.S. federal law that prohibits U.S. citizens and entities from bribing foreign government officials to benefit their business interests. |
|
|
Fighting Against Forced Labour and Child Labour in Supply Chains Act |
This act aims to increase industry awareness and transparency and drive businesses to improve practices by introducing measures through Bill S-211. |
|
This act requires companies to adapt and update their compliance, purchasing, and contract drafting processes, in addition to implementing due diligence programs. |
|
|
The UK Bribery Act 2010 is designed to combat bribery in the UK and consolidates previous offenses relating to bribery. |
|
|
The UK Modern Slavery Act 2015 requires businesses with a turnover of more than £36 million to publicly report on the steps they are taking to prevent modern slavery in their operations and supply chains. |
Industry Guidelines
There has been a noticeable increase, in recent years, in the prominence of regulatory compliance requirements focused on third-party risk assessments and monitoring, particularly for financial institutions, utilities, and critical infrastructure. These measures aim to ensure the security, integrity, and continuity of operations by addressing potential risks associated with outsourcing critical functions to external vendors, suppliers, and service providers.
Compliance with these regulations not only mitigates risks but also promotes accountability, transparency, and trust in vendor relationships. Organizations operating within these regulated sectors must prioritize robust vendor risk management practices to navigate the evolving regulatory landscape and ensure the protection of their operations and stakeholders.
Key TPRM Compliance Industry Guidelines
| Guideline | Summary |
|---|---|
|
Focuses on information security and cybersecurity resilience for Australian financial institutions. |
|
|
A European Union regulation addressing operational resilience and risk management in the financial sector. |
|
|
Provides guidance on outsourcing arrangements for banks in the European Union. |
|
|
Outlines guidance for the UK financial industry on outsourcing and third-party risk management. |
|
|
Offers guidelines for assessing IT and cybersecurity risks for U.S. financial institutions. |
|
|
Focuses on managing third-party risks in the U.S. financial sector. |
|
|
Involves verifying the identity and assessing the risks associated with clients in financial services. |
|
|
Provides guidance on outsourcing arrangements for financial institutions in Singapore. |
|
|
Ensures the security of critical infrastructure assets in North America. |
|
|
NERC (Security Guideline for the Supply Chain Cyber Security Risk Management Lifecycle) |
Focuses on cybersecurity risk management in the supply chain for critical infrastructure. |
|
NERC (Security Guideline for the Vendor Risk Management Lifecycle) |
Guides managing cybersecurity risks associated with vendors in critical infrastructure. |
|
Addresses cybersecurity requirements for financial institutions operating in New York. |
|
|
Provides guidance on outsourcing risk management for financial institutions in Canada. |
|
|
Focuses on prudential requirements and expectations for banks and insurers in the United Kingdom. |
Data Privacy Regulations
Data privacy regulations ensure that third-party vendors and service providers can safeguard personal information and prevent its misuse. TPRM is key in adhering to data privacy regulations such as GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act) when organizations use third-party service providers to manage their customer’s data. Understanding the nuances of these regulations is paramount for organizations operating in a global and digitally interconnected landscape.
Key Data Privacy Compliance Regulations
| Regulation | Summary |
|---|---|
|
A California law that grants privacy rights to consumers and regulates the collection and use of personal information by businesses. |
|
|
European Union regulations governing the protection of personal data, including its collection, storage, and processing. |
|
|
A U.S. federal law that safeguards the privacy and security of medical and health-related information. |
|
|
National Institute of Standards and Technology's special publication offering guidelines for securing healthcare information, particularly in compliance with HIPAA. |
|
|
NY SHIELD Act (New York State Stop Hacks and Improve Electronic Data Security Act) |
A New York state law that mandates data security measures and breach notification requirements. |
|
Singaporean legislation governing the collection, use, and disclosure of personal data. |
|
|
This provision mandates and empowers Québec's data protection authority, overseeing the collection, use, and communication of personal information and enforcing requirements like privacy impact assessments for transferring data outside the province. |
How to Build a TPRM Compliance Program
When delving into the intricate world of third-party risk management (TPRM) compliance, a systematic approach is paramount. Organizations should embark on a journey that not only meets regulatory requirements but also fortifies the resilience of their extended business ecosystem. Here are 10 crucial steps to initiate and strengthen TPRM compliance:
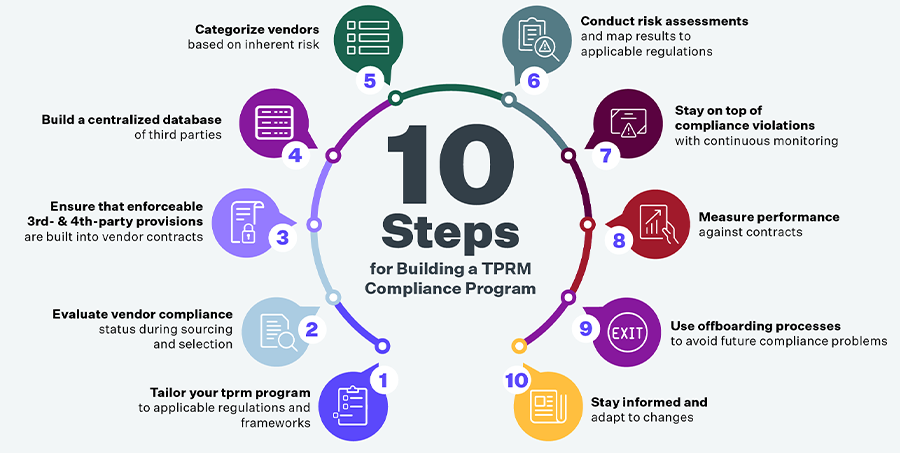
Step 1: Tailor your TPRM Program to Applicable Regulations and Frameworks
Examine the regulatory landscape to identify industry-specific and geographical requirements, and then pinpoint the suitable framework for customizing your compliance strategy to seamlessly align with these regulations.
Step 2: Evaluate Vendor Compliance Status During Sourcing and Selection
Include high-level compliance criteria in RFIs and RFPs and pre-screen third parties against vendor risk intelligence networks that provide access to completed assessments mapped to regulatory frameworks and industry standards.
Step 3: Ensure That Enforceable Third- and Fourth-Party Provisions Are Built into Vendor Contracts
Centralize the distribution, discussion, retention, and review of vendor contracts to ensure that all required provisions such as the right to audit are included and enforced through the vendor relationship. Seek solutions that seamlessly integrate contract lifecycle management with third-party risk management, so all internal teams are using the same workflow.
Step 4: Build a Centralized Database of Third Parties
Conduct a thorough accounting of all third-party relationships within your business ecosystem and build a central repository of vendor and supplier profiles. This will serve as a single point of reference for all internal departments to collaborate and report on your third-party compliance and risk management initiatives.
Step 5: Categorize Vendors Based on Inherent Risk
Inherent risk is a vendor’s risk level before accounting for any specific controls required by your organization. Use inherent risk scores to tier vendors and determine what type of ongoing due diligence they require. Compliance and regulatory factors can play heavily into this. For example, if GDPR is a significant driver for your organization, then tiering vendors based on their access to your customer’s data should be a primary consideration.
Step 6: Conduct Risk Assessments and Map Results to Applicable Regulations
Ensure ongoing compliance through periodic audits and assessments. Leverage automated vendor risk assessment solutions to streamline the process, manage evidence collection, and map responses to multiple regulations at once. This approach can vastly simplify and speed up your compliance reporting initiatives and should include built-in remediation recommendations to reduce the level of ongoing residual risk.
Step 7: Stay on Top of Compliance Violations with Continuous Monitoring
Leverage automated third-party risk monitoring solutions between periodic assessments. These solutions can surface new compliance issues by analyzing sources of cyber intelligence, business updates, financial insights, media screening, sanctions lists, breach events, and more.
Step 8: Measure Performance Against Contracts
Conduct regular performance assessments and contract reviews to ensure that third-party partners are adhering to any compliance mandates and applying any required remediations.
Step 9: Use Offboarding Processes to Avoid Future Compliance Problems
Terminated vendors may have access to sensitive data that may be subject to regulatory requirements, so follow a formalized offboarding process to ensure that all relevant data is appropriately destroyed or decommissioned.
Step 10: Stay Informed and Adapt to Changes
Stay informed about changes in the regulatory landscape and industry standards. Adapt your TPRM compliance strategy to incorporate new requirements and best practices, ensuring continuous relevance.
Conclusion
TPRM compliance is a dynamic and multifaceted endeavor that requires a holistic approach to assessing and continuously monitoring vendors and suppliers. By understanding the intricacies of risk assessments, continuous monitoring, cybersecurity frameworks, ESG regulations, industry guidelines, and data privacy regulations, your organization can fortify its third-party relationships, safeguard against potential threats, and thrive in an environment of trust and resilience. Embrace TPRM compliance not just as a regulatory obligation but also as a strategic imperative for the sustained success of your business in an interconnected world.
Next Steps: Discover Prevalent’s TPRM Compliance Solutions
Third-party vendors and suppliers are increasingly linked to data breaches, supply chain disruptions, and regulatory violations. As organizations face heightened societal and legislative scrutiny, ensuring resilience, responsibility, and ethical practices across their entire operations is imperative. Now, more than ever, organizations must ensure that their vendors can safeguard sensitive data, comply with crucial regulations, and uphold ethical business standards. Manually collecting, managing, and reviewing risk status, on the other hand, is unreliable, error-prone, and expensive. Through our single, integrated Third-Party Risk Management (TPRM) platform, Prevalent makes enforcement and risk prevention easier and faster. Request a demo to see if Prevalent is a fit for you.
-

NIS2 and Third-Party Risk Management
Leverage these best practices to address NIS2 third-party risk management requirements.
12/03/2024
-

SEC Cybersecurity Disclosure Rules: 9 Key Questions to Ask Third Parties
Ask your vendors and suppliers about their cybersecurity risk management, governance, and incident disclosure processes to...
10/24/2024
-

NIST CSF 2.0: Implications for Your Third-Party Risk Management Program
Enhanced cybersecurity supply chain risk management guidance has arrived with the final NIST CSF 2.0. Check...
09/25/2024
-
Ready for a demo?
- Schedule a free personalized solution demonstration to see if Prevalent is a fit for you.
- Request a Demo




