Third-Party Risk Monitoring Explained

Trying to manage vendor data security, information security, and broader third-party risk can be a hefty task. Implementing an effective third-party monitoring (TPM) program significantly reduces risk while enabling you to manage vendors with confidence.
Monitoring third parties continues to grow in importance. Threat actors have begun heavily targeting organizations in the cyber supply chain as they seek to compromise both upstream and downstream companies. At the same time, geopolitical risks, ESG risks and compliance requirements continue to mount.
A continuous third-party monitoring solution should be included in every third-party risk management program to ensure real-time risk analysis and reaction. A comprehensive third-party monitoring program can help you mitigate the impact of vendor data breaches, supply chain disruptions, and negative press on your organization. In this article, we provide an overview of third-party risk monitoring methodology and key terms. We also discuss the many benefits of implementing an effective program.
Third-Party Risk Monitoring Explained
Watch this overview to learn how to gain continuous visibility into cyber, business, financial and ESG threats traced to vendors and suppliers.
What Is Third-Party Risk Monitoring and How Does It Work?
Third-party risk monitoring is the practice of continually gathering and analyzing externally observable data on vendor cybersecurity posture, business ethics, financial status, and geopolitical context to identify potential supply chain risks. Third-party monitoring is essential for preserving a stable vendor ecosystem and ensuring data security, particularly in high-risk fields such as healthcare or financial services.
Organizations and stakeholders can achieve continuous insight into the compliance posture of vendor organizations by integrating deep security data collection and analysis with a third-party risk management approach, assisting in the defense of internal systems, conducting site visits and reviewing records.
Why Is Third-Party Risk Monitoring Important?
As international supply chains have become increasingly connected, third-party risk has grown exponentially. Actively monitoring third parties for cybersecurity, financial, ethical, reputational, and operational risk is critical to ensuring the stability and resilience of your organization's supply chain. Third-party monitoring ensures sustainability, trust and transparency in a vendor relationship. Below are some prominent examples of where enhanced third-party monitoring could have helped organizations avoid problems.
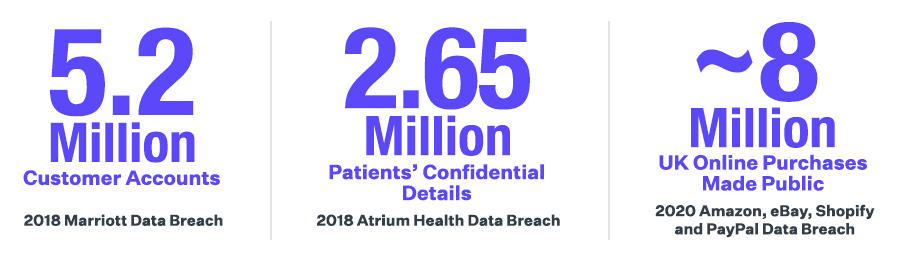
- Marriott Breach — In 2018 Marriott suffered a data breach due to their merger with Starwood. In early 2020 Marriott announced that another data breach resulted in the leak of 5.2 million customer accounts including addresses, birthdays, phone numbers, and loyalty cardholder information. This data breach was caused by two Marriott franchise owners who had their corporate access to systems hacked. Even in the case of a close trusted partner like a franchisee, we recommend keeping a close eye on all third parties who have access to your corporate infrastructure. These franchisees often don’t have the same cybersecurity standards as their parent companies, causing vulnerabilities for the entire organization.
- Magecart — Magecart, a group of cybercriminals, has carried out numerous attacks on large retailers around the world since 2015. Recent attacks on Ticketmaster, British Airways, Newegg, Feedify, and other companies are thought to be the work of the group. Magecart hackers typically infect third-party web servers used by their victims in order to steal sensitive information, such as credit card information.
- Security breach at Atrium Health — In 2018, Atrium Health experienced a data breach experienced a data breach that exposed the confidential details of over 2.65 million patients. A compromise of servers used by Atrium Health's billing provider, AccuDoc Solutions, caused the leak.
- Amazon data breach — A major data breach hit Amazon, eBay, Shopify, and PayPal in 2020. A third-party database of roughly eight million UK online retail purchases was made public. This isn't the first time Amazon has been the victim of a third-party-caused incident. In 2017, attackers hacked many Amazon-affiliated third-party vendors and used their accounts to post bogus offers.
- Data breach at General Electric (GE) — GE announced a data breach in 2020, which was caused by their service provider Canon Business Process Services. A hacked email server resulted in the public disclosure of publicly identifying information about current and former GE recipients and staff.
- Shutdown at Toyota — In February 2022, Toyota shut down operations in Japan after a major plastic supplier, Kojima Industries, suffered a data breach. Kojima had remote access to Toyota manufacturing plants, greatly increasing Toyota’s risk. As a result of the temporary shutdown, Toyota suffered financial and operational losses.
TPM Methodology
To accurately evaluate third-party risk, it’s essential to complement periodic “inside-out” vendor assessments with continuous “outside-in” threat monitoring. These third-party risk assessments, questionnaires, and the use of third-party monitoring enable organizations to be confident in third-party relationships moving forward.
Inside-Out Third-Party Assessment
This type of TPM approach focuses on vendor risk questionnaires, due diligence, and documentation that the vendor provides. Taking a close look at the vendor's security documentation and approach can prove to be invaluable for TPM programs. Look to ensure that the vendor’s security policies lineup with their answers on the assessment questionnaire and compliance requirements. In addition, you want to vet not only the third-party organization, but also the 4th and Nth parties that they work with.
Outside-In Third-Party Risk Monitoring
It is also critical to take an outside view of an organization. Do they have exposed credentials on the dark web? If they are a large company, are there publicly available financial records that could enable your organization to get a picture of their financial solvency? Make sure to conduct rigorous due diligence, including using TPRM tools and publicly available information.
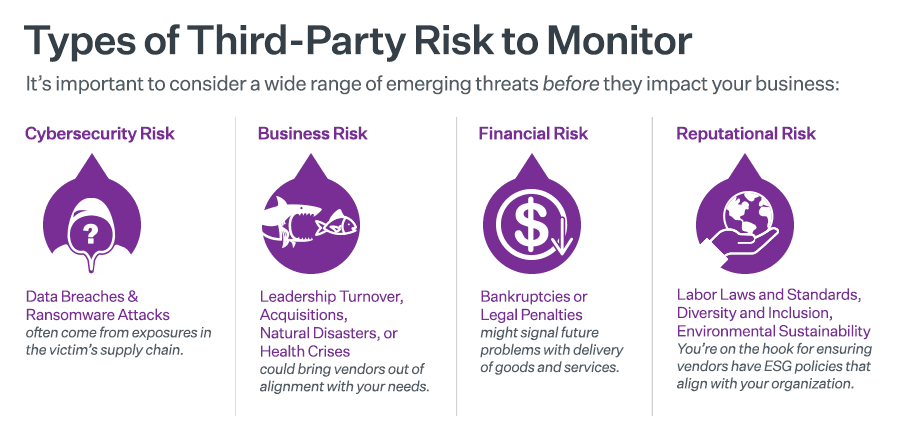
Types of Third-Party Risk Monitoring
Cybersecurity Risk Assessment and Monitoring
Cyber challenges abound in the online community. There isn't a week that goes by without news about major data breaches, some of which go undetected for months before being found. Cyber attackers are becoming more advanced in their methods of gaining access to personal and business information by focusing on the weakest access point: the company's third-party vendors. Third-party vendors can be linked via IT systems or integrations, and they can be SaaS vendors or data processors. These third parties can lack the same level of cyber protection as their clients, making them an easier target for hackers. Prevalent delivers cyber risk intelligence on over 550,000 companies by monitoring 1,500+ criminal forums; thousands of onion pages, 80+ dark web special access forums; 65+ threat feeds; and 50+ paste sites for leaked credentials — as well as several security communities, code repositories, and vulnerability databases.
Diversity Risk Assessment and Monitoring
In a more socially conscious world, doing business with third parties means ensuring that vendors not only follow national labor laws and standards, but also ensure that their workforce accurately reflects society as a whole. Most third-party risk assessment products, on the other hand, are primarily focused on cybersecurity threats, ignoring diversity and inclusion problems, which can result in negative press and reputational harm. The Prevalent Third-Party Risk Management Platform provides tools for evaluating third-party recruiting policies for diversity and inclusion. It also comes with built-in integration with ongoing reputational and regulatory insights to help you verify your appraisal findings.
Reputational and Financial Risk Monitoring
Third-party vulnerabilities encompass much more than just cybersecurity issues. Financial uncertainty, for example, can have an impact on a vendor’s ability to supply parts and services. A visit from OSHA may result in a facility closure. An unfavorable finding from a regulatory or ethics review can divert management’s attention and jeopardize your business. Although it is important to keep on top of all incidents that put vendors at risk, cybersecurity breaches often overshadow other types of risk events in the news. It’s no wonder that the majority of third-party risk management systems fail to provide critical financial and reputational intelligence to their clients. Prevalent’s Third-Party Risk Management Platform constantly tracks public and private databases of reputational risks and financial data, providing the insights, monitoring data and reports required to keep ahead of possible supplier disruptions.
Modern Slavery Risk Assessment and Monitoring
Governments around the world are actively combating modern slavery, which includes trafficking and forced labor of adults and children. The UK Modern Slavery Act of 2015, the Australia Modern Slavery Act, and the California Transparency of Supply Chains Act are also examples of legislation that seek to end modern slavery. Organizations must ensure accountability in their supply chains’ labor policies to comply with these rules or face fines, court sanctions, and poor press coverage. Businesses must perform supply chain survey-based assessments of supplier controls, monitor systems and validate the results with continuous external monitoring of their real-world practices.
Geopolitical Risk Monitoring
Monitoring for geopolitical risk continues to grow in importance in 2023. Relations between the U.S. and China continue to deteriorate, while tensions with countries including Russia, Iran and North Korea are increasing. As tensions grow, so does the risk of sudden business disruption stemming from trade actions, APTs and other events. The trade actions taken against China in the fall of 2022 showcases the sudden supply disruptions that can occur due to nation state activities. Conducting robust geopolitical risk monitoring can provide early warning of potential trade actions, tariffs, legal actions, and other geopolitically driven risks.
ESG Risk Monitoring
ESG risks are front and center for many organizations in 2023. New ESG regulations, such as the European Corporate Due Diligence Draft Directive and the German Supply Chain Due Diligence Act, are creating mandates for companies to audit their supply chains against ESG concerns. These are in contrast to the previous generation of ESG laws, which simply required organizations to report on ESG actions taken. When monitoring for ESG risks, it is essential to go beyond third parties and monitor the entire extended supply chain. Many organizations have suffered enormous reputational damage in recent years as a result of their failure to effectively identify significant ESG harms from downstream fourth- and Nth-party suppliers.
Continuous Third-Party Monitoring
In the time between vendor risk assessments, a lot can happen. That is why it is important to provide ongoing visibility into vendor threats. External risks to third parties are constantly tracked and analyzed by Prevalent’s Vendor Threat Monitor. The approach looks for cyber risks and vulnerabilities on the Internet and the dark web, as well as public and private streams of reputational information, and financial data. The Vendor Threat Monitor module is combined with inside-out Vendor Risk Assessment as part of the Prevalent’s Third-Party Risk Management Platform. Tacking and evaluation data for each provider are consolidated in a single risk registry, enabling you to easily compare results and streamline risk analysis, reporting, and response initiatives.
4th Parties and Beyond
Suppliers, retailers, investors, and others who do business with a company are considered third parties. However, there is another dimension to which all companies must pay attention: the partners and suppliers of their third parties, also known as fourth parties. Fourth partners (or "Nth parties," as they are referred to in the supply chain) are not contractually linked to an entity, but they are linked to its third parties.
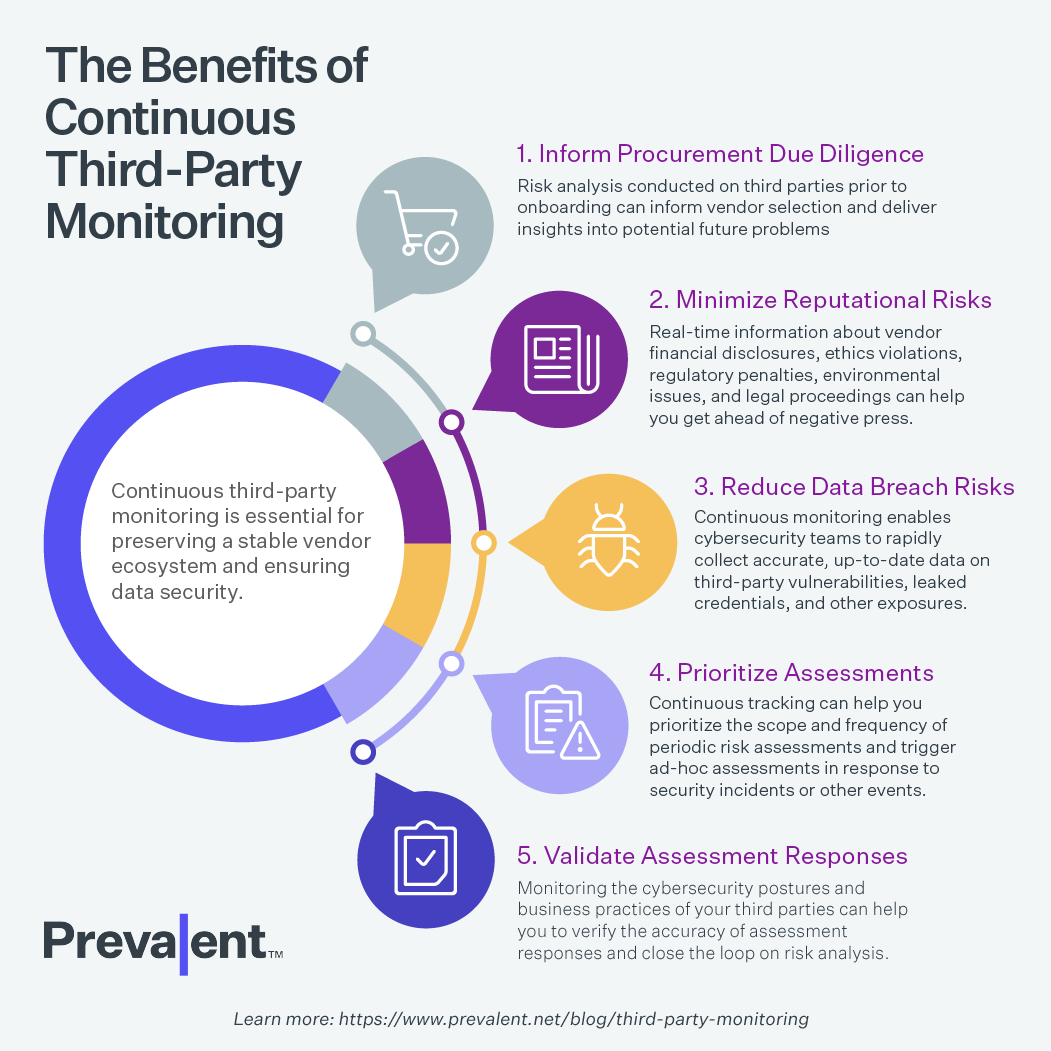
Benefits of Continuous Third-Party Risk Monitoring
1. Inform Procurement Due Diligence
Risk analysis conducted on third parties prior to onboarding can inform vendor selection and deliver insights into potential future problems. It can also inform the need for additional assessments to gather additional information about vendor security controls, compliance initiatives, and other factors that can impact your organization's operational workflow. Having upfront intelligence can save significant time and money, particularly if your organization has a complex supply chain involving numerous vendors.
2. Minimize Reputational Risks
Continuous monitoring provides you with real-time information about the reputational risk status of your third-party vendors. Intelligence on financial disclosures, ethics violations, regulatory penalties, environmental issues, and legal proceedings can help you get ahead of negative press in your supply chain and your organization’s potential “guilt by association.”
3. Reduce Data Breach Risks
Continuous monitoring enables cybersecurity teams to rapidly collect accurate, up-to-date data on third-party vulnerabilities, leaked credentials, and other exposures. This information can help your team to raise defenses, set limits, and/or issue warnings in response to a compromised website or a security violation -- so you can act immediately to protect your sensitive systems and customer data.
4. Prioritize Assessments
Continuous monitoring can help to build vendor profiles and determine their inherent risk. This information can help you prioritize the scope and frequency of periodic, questionnaire-based risk assessments based on each third party’s potential risk and criticality to your business. In addition, monitoring can trigger additional, ad-hoc assessment if a major security incident or organizational event is identified.
5. Validate Assessment Responses
Monitoring the cybersecurity postures and business practices of your third parties can help you to verify the accuracy of assessment responses and close the loop on risk analysis. Do they regularly scan for malware and patch their systems? Do they follow ethical hiring practices? Continuous monitoring is a great way to determine if your third-party vendors are adhering to your security, compliance, and ethics requirements.
Building Your Third-Party Risk Monitoring Program
With third-party cyber attacks on the rise and privacy issues pushing new laws, it's more important than ever to ensure that your vendors can safely handle confidential data. Manually collecting, managing, and reviewing risk status, on the other hand, is unreliable, error-prone, and expensive. Through our single, integrated Third-Party Risk Management (TPRM) platform, Prevalent makes enforcement and risk prevention easier and faster. Request a demo to see if Prevalent is a fit for you.
-

The Top 7 TPRM Predictions for 2025
2025 promises to be a consequential year for third-party risk management. Read our top TPRM predictions...
12/12/2024
-

Developing a Third-Party Risk Management Policy: Best Practice Guide
Learn how a third-party risk management (TPRM) policy can protect your organization from vendor-related risks.
11/08/2024
-

Vendor Offboarding: A Checklist for Reducing Risk and Simplifying the...
Follow these 7 steps for more secure and efficient offboarding when third-party relationships are terminated.
10/17/2024
-
Ready for a demo?
- Schedule a free personalized solution demonstration to see if Prevalent is a fit for you.
- Request a Demo




