Third-Party Risk Management: The Definitive Guide

In a world with increasingly interconnected companies, vendors, suppliers, logistics partners, and cloud services providers, Third-Party Risk Management (TPRM) has advanced from being an annual checklist exercise to a critical daily function. When an incident on the other side of the world can cause disruptions in your client service, it is critical to understand and manage those risks effectively and efficiently. Aside from the necessity of TPRM, the practice has advanced significantly from an exchange of emails 10 years ago to a continuous monitoring process that incorporates traditional due diligence with high degrees of automation.
This article explains TPRM and what drives its implementation. It also identifies the basic lifecycle of TPRM programs and finally outlines tips for success and traps to avoid at all costs as you implement your program.
Third-Party Risk Management in 90 Seconds
Third-Party Risk Management, or TPRM, is a critical daily function for many organizations. Learn about third-party vendor risks, and what to do about them, with this quick overview.
Ongoing geopolitical crises, catastrophic climate events, unexpected supply chain disruptions, and increasing third-party cybersecurity threats have caused organizations to rapidly implement TPRM programs to manage the risks posed by third parties. Most TPRM executives use their TPRM programs to manage cyber security risks, enable data governance, and manage privacy requirements while improving cost efficiency.
Additionally, organizations that can mature their TPRM capabilities rapidly are realizing significant competitive advantages. Organizations with mature TPRM programs have a much lower chance of negatively impacting their reputations and customers while managing global, regional, and organizational disruptions. Preventing mistakes or misconfigurations in your extended supply chain from impacting your ability to serve customers is likely a critical function for your organization. A TPRM program enables your organization to effectively identify, mitigate, and/or accept those risks. In short, a properly configured TPRM program can prevent unwanted surprises that negatively impact your organization.
Definition of Third-Party Risk Management
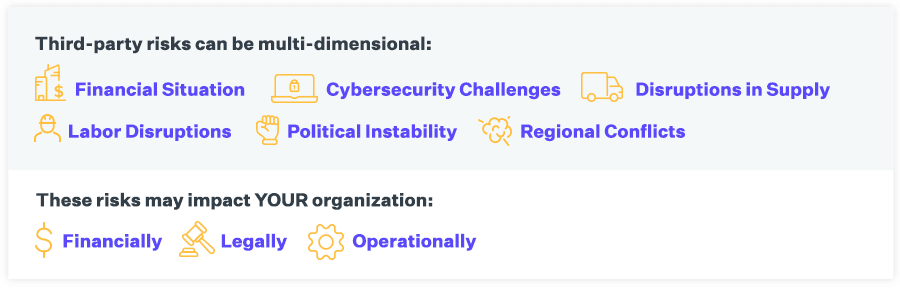
Third-party risk management (TPRM) is the process of identifying, assessing, and mitigating the risks associated with engaging external third parties such as vendors, suppliers, contractors, and business partners. It involves thorough due diligence to address potential risks that could affect an organization’s operations, financial health, cybersecurity, legal standing, or ability to serve its customers. These risks may encompass cybersecurity incidents, supply chain disruptions, labor shortages, financial instability, political factors, and regional conflicts. TPRM enables organizations to proactively manage risks and plan responses rather than reacting to issues as they arise, ensuring business continuity and protecting key stakeholders.
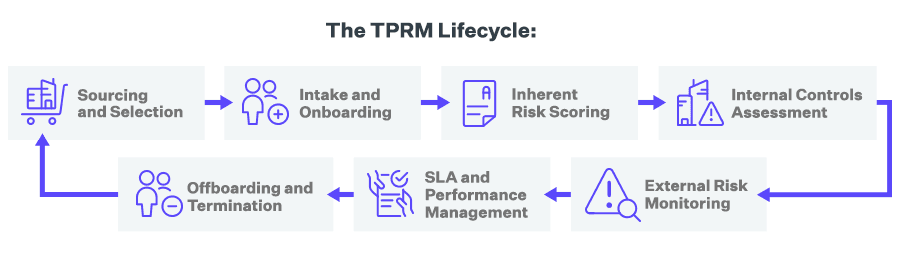
The value of TPRM begins with the process of identifying risks and extends throughout the entire lifecycle of the relationships between your organization and your vendors. The TPRM lifecycle includes:
- Sourcing and Selection - This phase includes evaluating each potential vendor's ability to meet service or solution requirements and scoring baseline security, privacy, reputational, and financial risks. This can be accomplished by conducting questionnaire-based assessments, accessing vendor intelligence databases, or a combination of both.
- Intake and Onboarding - Once vendors are selected, they are onboarded into a central repository via manual or bulk upload. This can be accomplished through intake forms completed by internal stakeholders, spreadsheet imports, or an API to an existing vendor management or procurement solution.
- Inherent Risk Scoring - Inherent risk is a vendor's risk level before accounting for any specific controls your organization requires. It is best practice to score a vendor's inherent risk with a simple assessment before giving them access to your systems and data. This also enables you to determine the required level of due diligence and the frequency and scope of subsequent risk assessments.
- Internal Controls Assessment - Controls assessments can be used during initial due diligence and periodically to satisfy audit requirements. Risks identified during the assessment process are usually scored according to impact, likelihood, and other factors. Results can also be mapped to key requirements in other compliance and security frameworks, such as ISO, NIST, or SOC 2.
- External Risk Monitoring - By tapping into external sources of continuous third-party intelligence, you can cover gaps between periodic assessments and validate assessment responses against external observations. Risk monitoring can include cyber intelligence, business updates, financial reports, media screening, global sanctions lists, state-owner enterprise screening, politically exposed person(PEP) screening, breach event notifications, and more.
- SLA and Performance Management - Assessments and monitoring can be used to determine whether vendors are meeting their obligations throughout the business relationship. For instance, this can include evaluating their ability to deliver against SLAs, apply remediations, or meet compliance requirements.
- Offboarding and Termination - During this phase, assessments ensure that all final obligations have been met. This can include contract reviews, settling outstanding invoices, removing access to systems and data, revoking building access, and reviewing privacy and security compliance.
When planning your TPRM approach, remember that the parties' circumstances may change at any point during the engagement. Detecting and managing those changes is critical to the success of your organization. Vendors may change business operations, their supply chain for key materials may be disrupted, or regional bodies may change import/export requirements. For example, laws regarding data privacy are changing rapidly all over the world. All of these conditions are happening today, and the companies that have effectively implemented a TPRM process are thriving while others are falling behind.
Given the rapid pace of change, there is a corollary need for organizations to monitor and perform an initial analysis of the available information in near real-time to identify and manage their risk. This requirement mandates that some of the processes automate the collection and dissemination of information about third-party vendors. Effective automation enables your TPRM office to identify risks and drive remediation before your organization suffers reputational risks.
Third-Party Risk Management Program Drivers
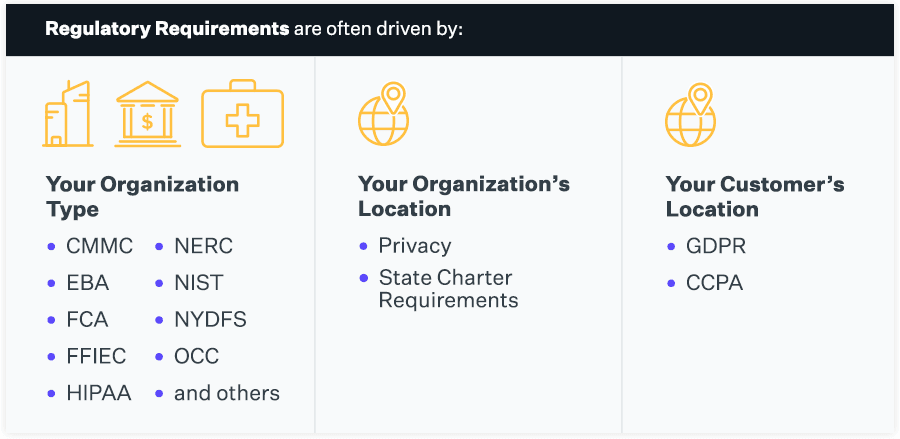
Several regulatory and compliance requirements mandate the management of third-party risk and can provide an effective framework for mitigating vendor risk. Regulatory requirements that drive TPRM programs cover a broad spectrum of markets, vendors, and data and are often driven by the type of organization (e.g., regulations and guidelines from CMMC, EBA, FCA, FFIEC, HIPAA, NERC, NIST, NYDFS, OCC, and others), the location of your organization (e.g., privacy, state charter requirements), or your customers’ location (e.g., GDPR, CCPA). The key point to understand regarding these requirements is ensuring that your program accounts for what data your organization is liable to protect, where your customers typically reside, and the standard requirements your vendors must meet to deliver their services. These requirements must be included in your agreements and extended to vendors working with the covered data.
Implementation of TPRM programs by organizations is driven by the following:
- Compliance with regulatory requirements.
- Cybersecurity risk.
- Competitive advantages of an effective TPRM program.
- Internal purchasing/efficiency drivers.
- Managing internal financial and operational risk.
- Meeting customer requirements.
Regardless of your organization's specific driver for establishing a TPRM program, it is critical to identify and work with all the internal stakeholders, such as executives, boards, procurement, internal audit, finance, IT, information security, legal, and compliance, in establishing your workflows.
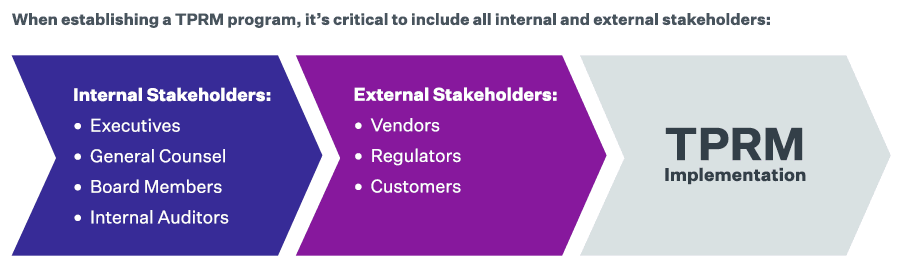
When considering implementing a TPRM program, it is critical to ensure that all of the impacted internal and external stakeholders are included in establishing the program. Including relevant stakeholders ensures that all people, processes, and technologies are aligned to produce an effective program. At a minimum, consider the following as internal stakeholders:
- Executives (CEO, CFO, CIO, COO, CISO, etc.)
- General Counsel
- Board members
- Internal auditors
There may be other internal stakeholders depending on your organization's type, function, and operations.
External stakeholders form another critical constituency for consideration in the development of your program. External stakeholders include:
- Vendors
- Regulators
- Customers
Since TPRM programs seldom start at a company's inception, it is important to consider the existing agreements/programs already in force with external vendors and ensure that they are thoroughly analyzed against the proposed TPRM program. Ensure that discrepancies are recorded and that a plan to address unmitigated risks is created and tracked to completion.
Regulatory TPRM Risk Management Drivers
Regulatory standards are a primary driver for TPRM programs. Regulatory programs are specific to:
- Healthcare
- Contracting for the federal government
- Credit card acceptance
- Financial services
- Banking
- Manufacturing

All of these require the implementation of a full lifecycle process for TPRM. These requirements are typically driven by the type of sensitive data collected in the standard course of business.
A primary example of this kind of regulatory-driven risk management is an important part of the industry-standard PCI-DSS, which defines third-party providers and requires that providers do not transmit cardholders "data on behalf of customers or organizations to providers that may compromise the security of their data and environment.” This means that while companies are obliged to work on the required cybersecurity program for themselves, they are still required to monitor vendors' cybersecurity programs with access to sensitive data, even if they keep the risk below a certain threshold.
Another example is federal programs and contracting that require strict security management of all vendors with access to the information. This process goes far beyond simple questionnaires and exchanging documentation; it may also include scanning internal environments and legal representations by executives regarding the data protection in place. The complexity of the third parties involved, the potential for conflicts of interest, and financial losses are driving companies to improve their risk management practices and risk mitigation strategies continuously.
Traditionally, TPRM was executed by internal personnel or outsourced to consultants who followed a thoroughly scripted process to gather, analyze, and report on the information. Specifically, organizations that have previously used personnel to help with the assessment process may need to rethink their approach as the current pandemic has limited travel and significantly limited real-time information gathering. This prevents on-the-spot assessment from being viable and completely upends the traditional approach to third-party risk assessment, which typically leverages in-person visits to monitor the results provided by questionnaires.
Coupling current conditions with the rapidly increasing risk complexity and reach of supply chains today, this simply isn’t feasible using traditionally successful processes. Success at TPRM requires increasing use of automation and tools designed to perform the collection and initial analysis of vendor data.
The Role of Artificial Intelligence in TPRM
As organizations increasingly rely on interconnected supply chains and third-party relationships, comprehensive risk insights and timely decision-making are imperative. The exponential growth of data from diverse sources offers an opportunity to leverage AI and advanced analytics, enabling deeper risk assessments, predictive capabilities, and real-time monitoring. The rise in regulatory scrutiny and the surge in sophisticated threats further necessitate data-driven and AI-driven approaches to risk management.
Adopting artificial intelligence (AI)-related technologies can be instrumental in strengthening a modern TPRM program. AI's transformative capabilities offer unparalleled opportunities to streamline TPRM and supplier risk management (SRM) processes, providing a more efficient and proactive approach to navigating the complexities of contemporary business networks.
Here are just a few of the ways you can leverage AI in your third-party risk management program:
- Task automation: AI-powered systems can streamline routine third-party risk assessments, data analysis, and reporting. This improves efficiency and accuracy while helping third-party risk managers to focus on higher-level activities.
- Predictive analytics: AI models can analyze historical data and patterns to predict potential risks, helping you to take proactive measures to mitigate them.
- Anomaly detection: AI algorithms can identify unusual patterns or behaviors that may indicate fraud, security breaches, or other risks.
Learn more in the white paper, How to Harness the Power of AI in Third-Party Risk Management.
What's Next for Third-Party Risk in 2024?
Join Prevalent as we review the year in third-party risk, explore emerging third-party risk management trends, and deliver a roadmap to help you prioritize your TPRM program in 2024.
What Is the Value of TPRM?
As supply chains spread worldwide, the potential risks increase beyond simple security assessments to clearly identify the security posture when onboarding new vendors. This may cause difficulty assessing your exposure to third-party disruptions due to large-scale "macro events" such as wars and geopolitical unrest, fuel prices, natural disasters, and other regional disasters. As the industry has learned through recent events, it has never been more important for companies to streamline the processes used to collect cybersecurity data from their providers. When it comes to third- and fourth-party networks, where visibility and control are reduced, risk factors within those organizations are often more challenging to monitor, evaluate, and mitigate as part of a TPRM.
A core part of your vendor risk management process goes beyond simply assigning security ratings to your service providers. A successful TPRM management solution grants you visibility into your third-party ecosystem and is organized around the following questions:
- Can you identify who could be affected and the services the third party provides to secure your data?
- Can you ascertain which third parties provide services to the organization and keep their data secure?
Ultimately, strengthening your organization, addressing gaps (understanding where the gaps are, implementing processes and protocols), and resolving third-party risk management issues will improve your business, helping you sustain and grow.
Implementing Your TPRM Program
Once you have decided to implement a TPRM program, you have a number of important questions that will form the basis of your program. These questions include:
- Do you hire a partner to help you start and implement the program?
- How do you manage the expectations of your internal stakeholders?
- Do you need to assign responsibilities in the event of a data breach?
- What are the exact requirements third parties must meet to do business?
- Do the external stakeholders understand the requirements and can implement them?
- Will the imposition of these requirements change the financial relationship with the vendors?
- How do you roll this program out into existing relationships?
Organizations must focus on bringing together the right people, processes, and technologies to implement a third-party risk management program. Understanding the balance and the requirements of each of these functions is critical to the successful operation of your program.
To address risk exposures in TPRM environments, you should enable organizational standards and language in the following areas:
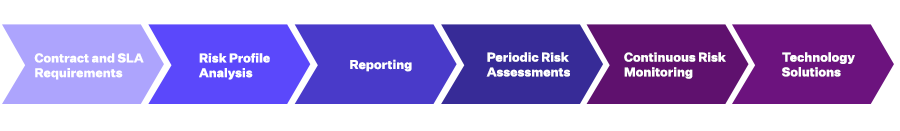
- Set up contract and service level agreement requirements to address risk-related commitments.
- Analyze the vendor risk profile with the risk profile of the engagement or the service provided.
- Enable a reporting process driven by dynamic monitoring and risk assessment based on events.
- Mix periodic risk assessments (self-reported) and continuous risk monitoring (externally reported) approaches for holistic risk identification.
- Implement technology solutions to integrate procurement, performance, and risk management on a unified platform that provides stakeholders with updated information on demand to meet their specific needs.
It is important to note that in building relationships with internal and external stakeholders, not all incentives have to be punitive or restrictive. Establishing contract or service level agreement requirements should include minimum performance standards but can also include "rewards" for compliance with critical risk management functions. Additionally, analyzing the vendor's requirements versus your organization's can provide enormous dividends for both parties. By leveraging areas of existing compliance, it is possible to lower the costs for both parties to their mutual benefit.
The value of an effectively implemented TPRM solution is in achieving a critical risk management program that provides early warning and drives effective risk mitigation. Understanding the value of TPRM is only the first step in deciding to implement the program. The choices, resources, integration with existing business processes, and relationships require the support of the organization and the onboarding of existing third-party ecosystems. While it is a complex undertaking, using questionnaires, templates, tools, standards for SLAs, and automation can be invaluable to rapidly maturing your TPRM program.
Navigating the Vendor Risk Lifecycle: Keys to Success
This complimentary guide details best practices for successfully managing risk throughout the vendor lifecycle. See what we've learned in our 20+ years of experience working with hundreds of customers.

Next Steps
Wondering how to get started? Check out our free best practices guide, Navigating the Vendor Risk Lifecycle: Keys to Success at Every Stage. Want to benchmark your existing TPRM practices and get a roadmap to program maturity? Request a free TPRM Program Maturity Assessment. Interested in whether our third-party risk management solutions and services may be a fit for your organization? Request a demo.
-

Developing a Third-Party Risk Management Policy: Best Practice Guide
Learn how a third-party risk management (TPRM) policy can protect your organization from vendor-related risks.
11/08/2024
-

Vendor Offboarding: A Checklist for Reducing Risk and Simplifying the...
Follow these 7 steps for more secure and efficient offboarding when third-party relationships are terminated.
10/17/2024
-

Preparing a Third-Party Incident Response Plan
Effectively manage third-party cybersecurity incidents with a well-defined incident response plan.
09/24/2024
-
Ready for a demo?
- Schedule a free personalized solution demonstration to see if Prevalent is a fit for you.
- Request a Demo




