Latest Analyst Report: The 2023 Gartner® Market Guide for Supplier Risk Management Solutions

Third-Party Vendor Risk Assessment
Automate and accelerate the vendor risk assessment process
Manually collecting, maintaining and analyzing vendor risk data is inefficient, error-prone and costly.
Prevalent automates risk assessments to extend the visibility, efficiency and scale of your third-party risk management program. With a library of 200+ standardized assessments, customization capabilities, and built-in workflow and remediation, the solution automates everything from survey collection and analysis to risk rating and reporting.
With Prevalent, you can easily gather and correlate intelligence on a wide range of vendor controls, including IT security, compliance, performance, contract adherence, business continuity, financial position, reputation, ethics, anti-bribery & corruption, ESG, diversity and more.
Part of the Prevalent Third-Party Risk Management Platform, the Vendor Risk Assessment module is integrated with continuous Vendor Risk Monitoring to deliver a 360-degree view of security and compliance.
Vendor Risk Assessment Explained
Vendor risk assessments not only enable your organization to proactively identify and mitigate third-party risks, but also be better prepared for when incidents do occur. Watch this quick overview to learn more.
Key Benefits
-
Reduce the manual labor behind vendor survey and response management by 50%
-
Zero-in on risks and control failures, and gain actionable remediation guidance
-
Clearly communicate actual business risk to stakeholders
-
Speed communications and status reporting with vendors
-
Increase risk visibility and measure program effectiveness
-
Integrate with ITSM, GRC and security scoring solutions for centralized risk management
-
Scale your program with flexible platform configuration options

Prevalent have provided us with a scalable, repeatable approach both in terms of efficiency and cost which really addresses the issues we were facing around our supplier risk management.
— Information Security & Assurance Specialist, Cancer Research UK
-
Vendor Assessment Library

Leverage 200+ pre-defined assessment templates including SIG Core, SIG Lite and H-ISAC standardized vendor risk assessment questionnaires, as well as GDPR, FCA, PCI-DSS, ISO 27001, CMMC, NIST, Modern Slavery, Anti-Bribery, Health & Safety, Management & Ethics and more with the Prevalent Compliance Framework (PCF). Import offline assessments or build custom questionnaires with risk and control elements relevant to your business. Vendors can also update you on events with proactive assessments.
-
Vendor Risk Ratings & Compliance Registers

Generate risk registers upon survey completion, integrating real-time cyber, and business and financial monitoring insights to automate risk reviews, reporting and response. Generate vendor risk assessment reports to document status by regulation.
-
Unified Risk Register for Assessment & Monitoring

Prevalent normalizes, correlates and analyzes information across inside-out risk assessments and outside-in monitoring from Prevalent Vendor Threat Monitor and BitSight. This unified model provides context, quantification, management and remediation support.
-
Virtual Third-Party Risk Advisor
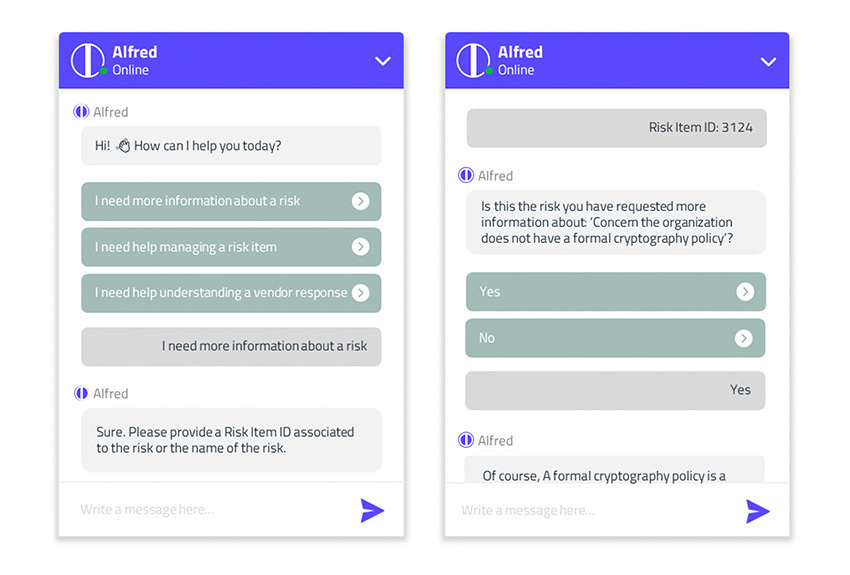
Leverage a conversational AI trained on billions of events and more than 20 years of experience to deliver expert risk management insights in the context of industry guidelines such as NIST, ISO, SOC 2 and others.
-
Automated Actions with Playbooks

Leverage a pre-packaged library of ActiveRules to automate a range of tasks normally performed as part of the onboarding assessment and review processes – such as updating vendor profiles and risk attributes, sending notifications, or activating workflow – utilizing if-this, then-that logic.
-
Vendor Risk Remediation Workflow

Efficiently communicate with vendors and coordinate remediation efforts. Capture and audit conversations; record estimated completion dates; accept or reject submissions on an answer-by-answer basis; assign tasks based on risks, documents or entities; and match documentation and evidence to risks. Includes built-in remediation guidance to accelerate risk mitigation.
-
Reporting & Analytics with Machine Learning

Reveal risk trends, status and exceptions to common behavior for individual vendors or groups with embedded machine learning insights. Quickly identify outliers across assessments, tasks, risks, etc. that could warrant further investigation.
-
Compliance-Specific Reporting
 Learn More About Prevalent's Compliance Solutions
Learn More About Prevalent's Compliance SolutionsAutomatically map information gathered from control-based assessments to regulatory frameworks including ISO 27001, NIST, CMMC, GDPR, CoBiT 5, SSAE 18, SIG, SIG Lite, SOX, NYDFS, and more to quickly visualize and address important compliance requirements.
-
Data & Relationship Mapping

Identify relationships between your organization and third parties to discover dependencies and visualize information paths.
-
Document & Evidence Management
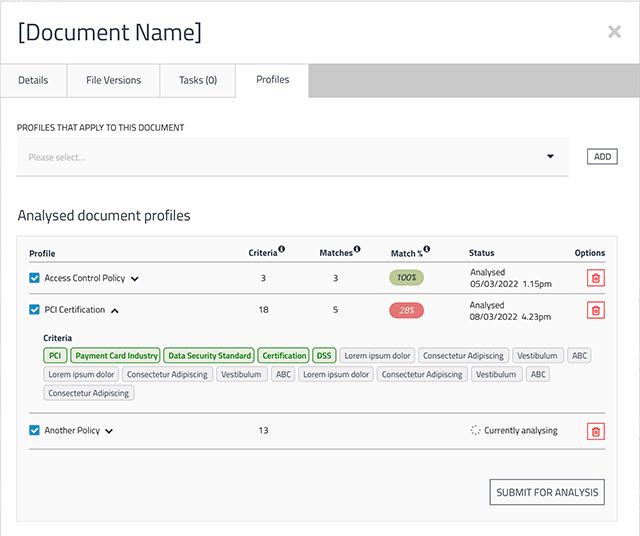
Centralize agreements, contracts and supporting evidence. Includes built-in automated document analysis based on AWS natural language processing and machine learning analytics to confirm evidence suitability.
-
Vendor & Entity Management
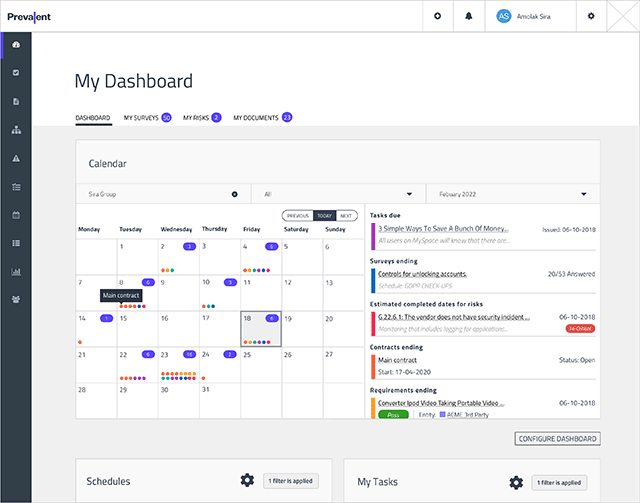
Simplify vendor management with custom dashboards that can include calendar views of actions, as well as survey schedules, tasks, audit trails, and requirements tracking. Build vendor profiles that include location, ownership, revenue, SIC code, fiscal year end, mapping of fourth parties, and other information for managing the full vendor lifecycle.
-
Connector Marketplace

Access dozens of pre-built connectors that use a low-code approach to integrate the Prevalent Platform with traditionally siloed tools. As a result, you can eliminate silos between applications and gain a more holistic view of enterprise risk management throughout the third-party risk lifecycle.
Vendor Risk Assessment: The Definitive Guide
Download this 18-page guide to gain comprehensive guidance on how to conduct and implement vendor risk assessments at your organization.

Who Wins
-
Procurement
Ensure that vendors align to strategic initiatives and deliver on their promises by continuously monitoring business continuity, performance, contracts and more.
-
IT Security
Eliminate spreadsheets once and for all by automating the scheduling, collection, analysis, management, and remediation of vendor risks in a central platform.
-
Risk Management
Gain a closed-loop view to validate vendor risks and remediations.
Let us do the heavy lifting
From managing your risk assessment process to monitoring vendors for emerging risks, our Vendor Risk Assessment Service frees your team to focus on remediating risk and keeping your business moving forward.

-
 Blog Post
Blog PostVendor Risk Assessment: The Definitive Guide
Conducting a vendor risk assessment prior to onboarding a new supplier or giving a third-party access...
-
 Blog Post
Blog PostSIG 2024: Key Updates and Considerations
Uncover key changes in the Standard Information Gathering (SIG) Questionnaire for 2024 and learn what these...
-
 Blog Post
Blog PostWhat to Look for in a Vendor Risk Assessment Report
Good vendor risk assessment reports help strengthen vendor relationships, demonstrate proper due diligence, and shed light...
-
Ready for a demo?
- Schedule a free personalized solution demonstration to see if Prevalent is a fit for you.
- Request a Demo










