
Third-Party Vendor Risk Monitoring
Validate vendor security controls with continuous cyber, operational, reputational and financial risk intelligence
A lot can happen between periodic vendor risk assessments. That’s why it’s essential to have continuous insights into vendor risks.
Prevalent Vendor Threat Monitor continuously tracks and analyzes external threats to your third parties. The solution monitors the Internet and dark web for cyber threats and vulnerabilities, as well as public and private sources of operational, reputational, sanctions and financial information.
Part of the Prevalent Third-Party Risk Management Platform, the Vendor Threat Monitor module is integrated with inside-out Vendor Risk Assessment. All monitoring and assessment data is centralized in a unified risk register for each vendor, enabling you to quickly correlate the findings and streamline risk review, reporting and response initiatives.
Third-Party Risk Monitoring Explained
A comprehensive third-party monitoring program can help you mitigate the impact of vendor data breaches, supply chain disruptions, and negative press on your organization. Watch this quick overview to learn more.
Key Benefits
-
Fill gaps between point-in-time assessments with round-the-clock, external monitoring for new and evolving third-party risks
-
Get ahead of supply chain breaches with intelligence on vendor vulnerabilities, network health, exposed data, and hacking incidents
-
Validate third-party security and compliance controls by comparing vendor assessment responses to externally observable risks and incidents
-
Gain a complete view of risk by combining cyber monitoring with continuous operational, financial and reputational updates
-
Centralize, correlate and analyze external monitoring data with internal assessment responses for a 360-degree view of vendor risk
-
Take action to reduce identified risks with automated risk response playbooks and remediation recommendations
-
Vendor Cyber Intelligence

Reveal third-party cyber incidents for 550,000 companies by monitoring 1,500+ criminal forums; thousands of onion pages; 80+ dark web special access forums; 65+ threat feeds; and 50+ paste sites for leaked credentials — as well as several security communities, code repositories, and vulnerability databases.
-
Vendor Operational Updates

Access qualitative insights from over 550,000 public and private sources of operational information, including M&A activity, business news, management and leadership changes, competitive news, new offerings, operational updates, and more.
-
Vendor Financial Insights

Tap into financial information from a global network of millions of businesses across 160+ countries. Access 5 years of financial performance data, including turnover, profit and loss, shareholder funds, credit ratings, payment history, bankruptcies, investments, and more. Screen new vendors, monitor existing vendors, and evaluate their health for informed sourcing decisions.
-
Vendor Reputational Insights
Avoid reputational damage to your company from working with corrupt vendors and individuals by efficiently:
- Screening for adverse media and negative news coverage from 30,000 global sources
- Monitoring global regulatory and legal sanctions from 1,000+ enforcement lists and court filings including OFAC, EU, UN, BOE, FBI, BIS, FDA, US HHS, UK FSA, SEC and more
- Screening for state-owned and government-linked enterprises to avoid conflicts of interest
- Screening against a global PEP database with over 1.8 million politically exposed person profiles, including their families and associates, to fight corruption and bribery
-
Breach Event Notification Monitoring
Access a database containing 10+ years of data breach history for thousands of companies around the world. Includes types and quantities of stolen data; compliance and regulatory issues; and real-time vendor data breach notifications. (Licensed separately)
-
Risk Profiling Snapshot
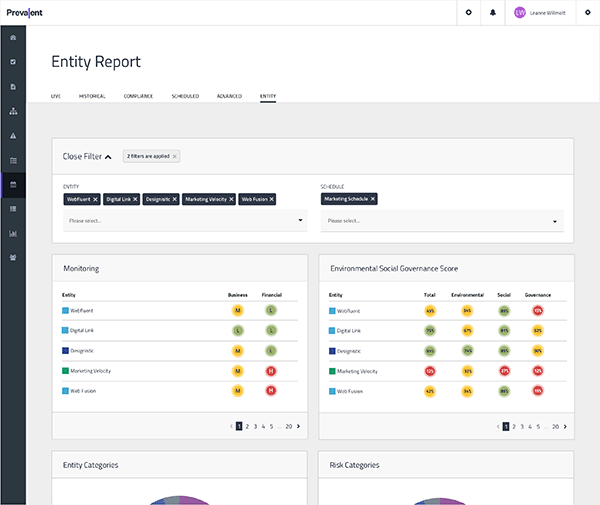
Gain a comprehensive view of a vendor’s demographic information, 4th-party technologies, ESG scores, plus recent business and reputational insights, data breach history, and recent financial performance to inform risk-based vendor selection decisions.

Prevalent detects my organization's risks automatically. They pull from several different sources and are able to provide actionable insights for me and my team.
— CISO, Large Technology Firm
Key Features
-
AI-Enabled Intelligence Platform
Leverage contextual machine learning algorithms to analyze data from thousands of sources.
-
Unified Risk Register
Simplify remediation by normalizing monitoring data into tangible risks, and link real-time cyber, business and financial events to assessment findings.
-

Vendor Risk Scaling
Quickly gauge risk via straightforward high/medium/low risk scoring.
-
Rule Automation
Leverage automated playbooks to simplify actions and workflow based on findings.
-
Centralized Risk Management
Display and track vendor threat monitoring status through a centralized management console.
-
AI-Generated Event Summaries
All events are sent to Prevalent’s dedicated large language model (LLM) to generate a summary of the event. Choose a paragraph or bullet point summary, with executive summaries available in reporting.
-
Email Summaries
Receive daily summaries of high-risk events triggered by cyber, business and financial monitoring.
-
Reporting & Analytics with Machine Learning
Identify, alert and communicate exceptions to common behavior with built-in and pdf-exportable cyber, business and financial monitoring report templates.
Who Wins
-
Procurement
Ensure that vendors deliver on their promises by continuously monitoring for sanctions, important news updates, and financial status.
-
IT Security
Reduce risk by validating the results of point-in-time controls assessments with continuous monitoring insights.
-
Risk Management
Gain round-the-clock cybersecurity and reputational insights to make informed risk-based decisions between assessments.
Executive Brief: How to Get More from Third-Party Risk Scores
Discover how to build a more comprehensive, actionable and cost-effective vendor risk monitoring program.

-
 White Paper
White PaperHow to Get More from Third-Party Risk Scores
This executive brief reveals how to build a more comprehensive, actionable and cost-effective vendor risk monitoring...
 Blog Post
Blog PostThird-Party Risk Monitoring Explained
A comprehensive third-party monitoring program can help you mitigate the impact of vendor data breaches, supply...
 Blog Post
Blog PostHow to Use Threat Intelligence to Reduce Third-Party Risk
Expand the scope of your TPRM program with these top sources of third-party risk intelligence.
-
Ready for a demo?
- Schedule a free personalized solution demonstration to see if Prevalent is a fit for you.
- Request a Demo





