Latest Analyst Report: The 2023 Gartner® Market Guide for Supplier Risk Management Solutions
Third-Party Risk Management at the Crossroads: Results from the 2022 TPRM Best Practices Study

Results from the definitive 2022 Third-Party Risk Management Study are in – and there is a lot to unpack as we review how organizations are responding to record numbers of third-party data breaches, supply chain disruptions due to continued pandemic shutdowns, and even the war in Ukraine.
This year’s study shows that third-party risk management (TPRM) is at a crossroads, demonstrating that companies have a choice of two paths to take – the existing path and the better path. To illustrate, consider the study’s conclusions:
| The Current Path | The Better Path |
|---|---|
|
Organizations are paying more attention to non-IT security risks … |
… but should be doing more in more risk areas. |
|
Third-party risk management may (finally!) be getting more strategic … |
… but organizations should work to eliminate stubborn manual methods for assessing third parties that make audits more complex and time consuming. |
|
Organizations are rightly concerned with increasingly damaging third-party security incidents … |
… but should unify their disparate toolset to reduce the time to detect and respond to third-party incidents. |
|
Organizations are doing a fair job of assessing vendor risks during the most obvious stages of the third-party lifecycle … |
… but should consider more stages to keep TPRM discipline from faltering as vendor relationships progress. |
In this post we’ll review the good (and bad) news and recommend three steps that organizations can take to improve their TPRM processes to get on the path to success.
The 2022 Third-Party Risk Management Study
Get on the path to TPRM success with insightful data, analysis and recommendations from our survey of global third-party risk management practitioners

40% of Organizations Are Paying More Attention to Non-IT Security Risks … but It’s Still Not Enough
TPRM programs are still primarily focused on addressing the risks faced when working with IT vendors (45%), but a surprising 40% of respondents in this year’s study say they are focused on managing both IT and non-IT vendor risks.
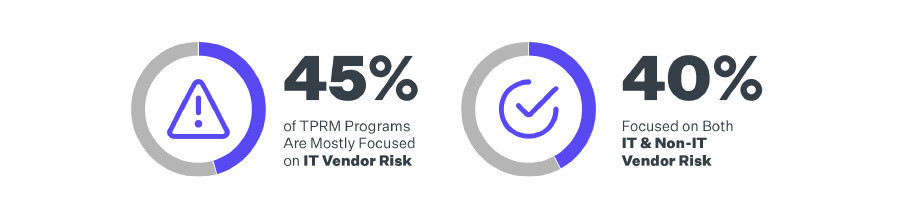
Also, as you can see in the graphic below, more teams are concerned with TPRM risks beyond IT security.
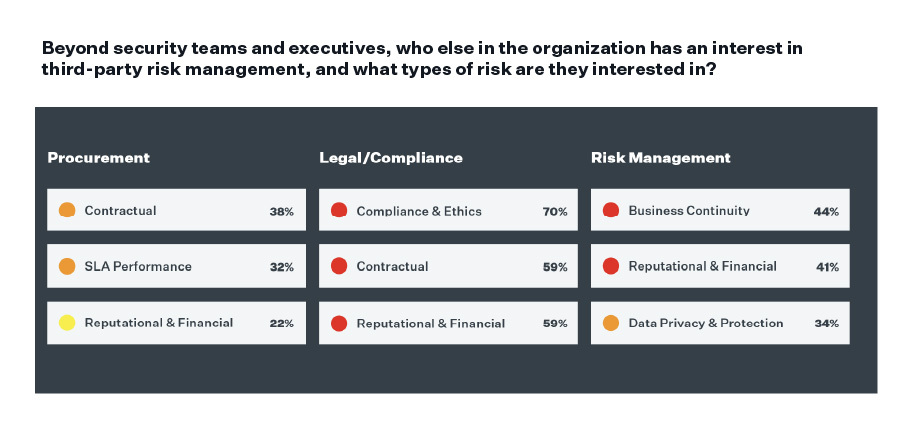
However, the lowest-weighted non-IT risks in importance were modern slavery, anti-money laundering, and anti-bribery and corruption risks. Following a similar theme to the Prevalent 2021 Third-Party Risk Management survey, organizations continue to overlook less quantifiable risks that could still lead to compliance violations, fines, or negative reputational impacts. For example, with the Russian invasion of Ukraine, companies with third-party suppliers in Russia must now consider whether they are exposed to bribery and money laundering as a result of sanctions.
Third-Party Risk Management May (Finally!) Be Getting More Strategic… but Those Pesky Spreadsheets Have Got to Go
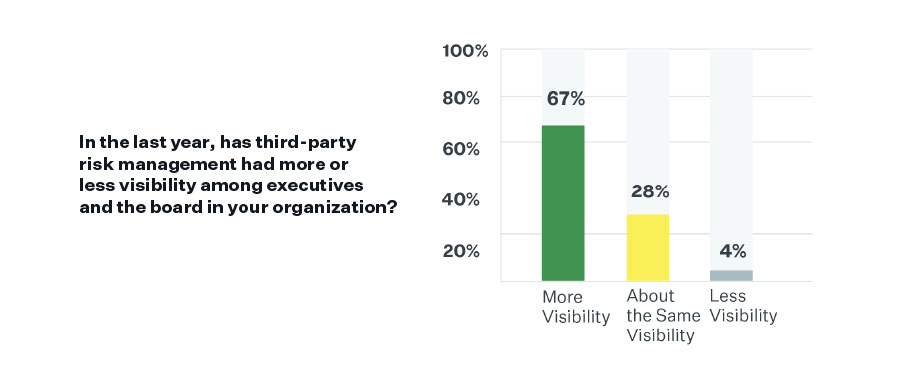
Two-thirds of respondents report that their TPRM programs have more visibility among executives and the board compared to last year. This is great news! TPRM is starting to be seen as strategic. However, it took massive increases in third-party vendor and supplier-related cybersecurity issues such as Log4j, the Toyota supply chain breakdown, and the Kaseya ransomware attack to get there.
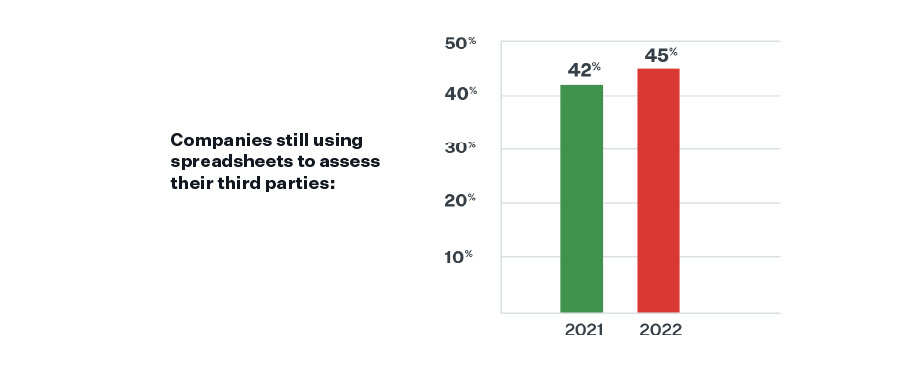
Unfortunately, manual processes are still holding organizations back, with even more companies (45%) reporting that they use spreadsheets to assess their third parties this year vs. 2021.
These manual processes add unneeded complexity and time to third-party risk audits, with 32% of respondents saying it takes more than a month (and in some cases more than 90 days) to produce reporting and evidence required to meet regulatory audits.
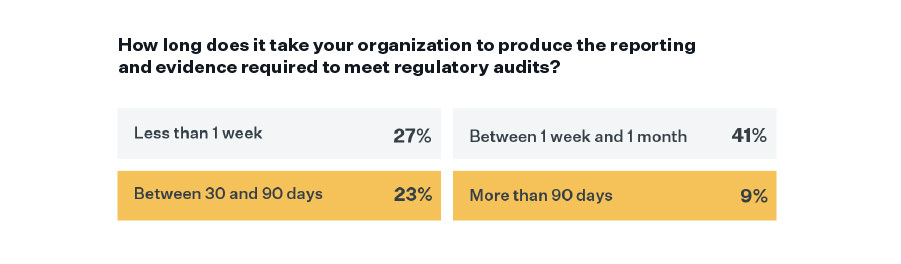
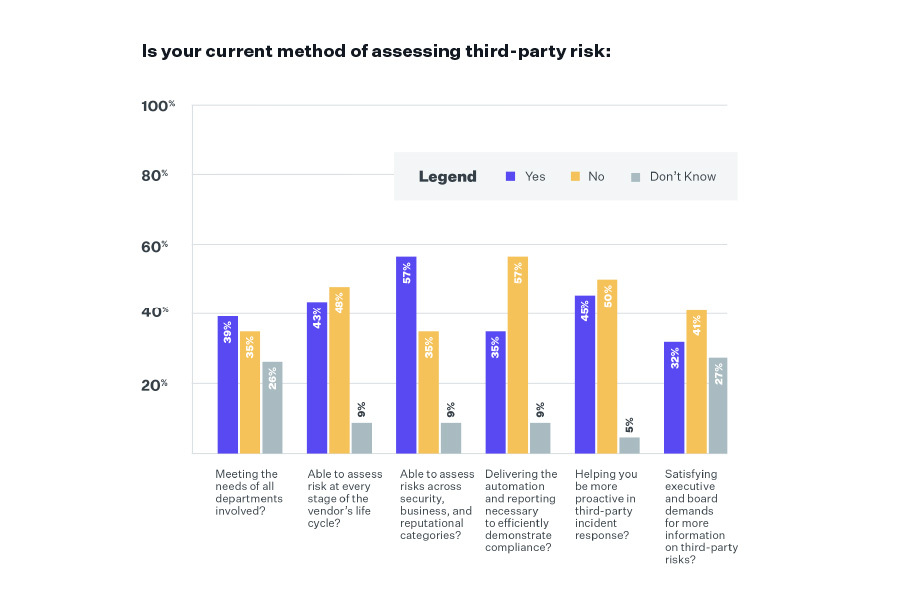
Something must be wrong with existing approaches, as high percentages of respondents say their current methods of assessing vendors are not able to deliver reporting to demonstrate compliance (57%), be more proactive in third-party incident response (50%), or assess risks at every stage of the vendor’s life cycle (48%).
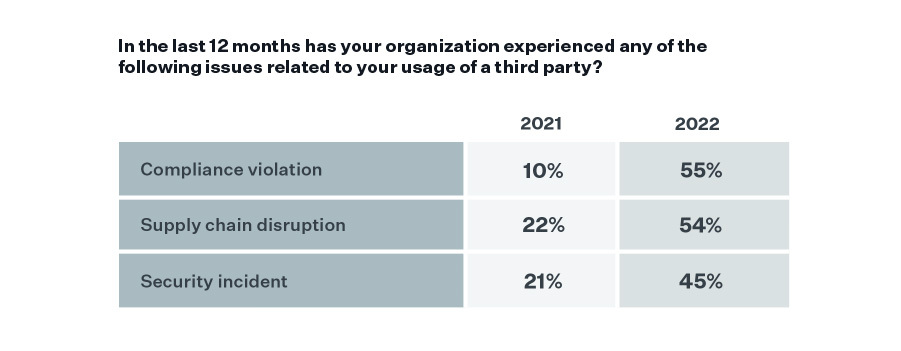
45% of Organizations Experienced a Third-Party Security Incident in the Last Year… but Are Using Disparate Tools That Lengthen Incident Response Timelines
The top concern facing organizations with regard to their usage of third parties is a data breach (69%), and 45% of respondents said they experienced a security incident in the last year – up from 21% in 2021!
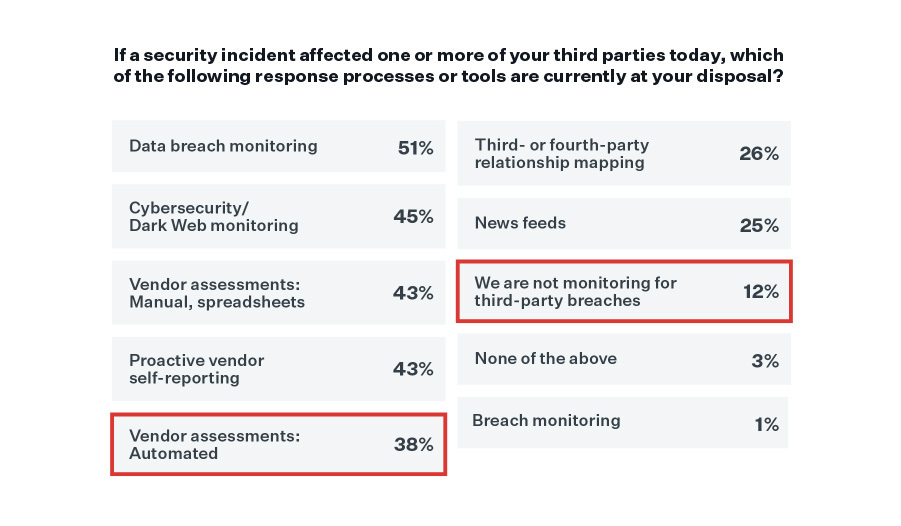
Top incident response tools that respondents reported having at their disposal included data breach monitoring (51%), cybersecurity/dark web monitoring (45%), vendor assessments (manual/spreadsheet-based) (43%), and proactive vendor self-reporting (43%). But only 38% indicated having access to automated vendor assessments.
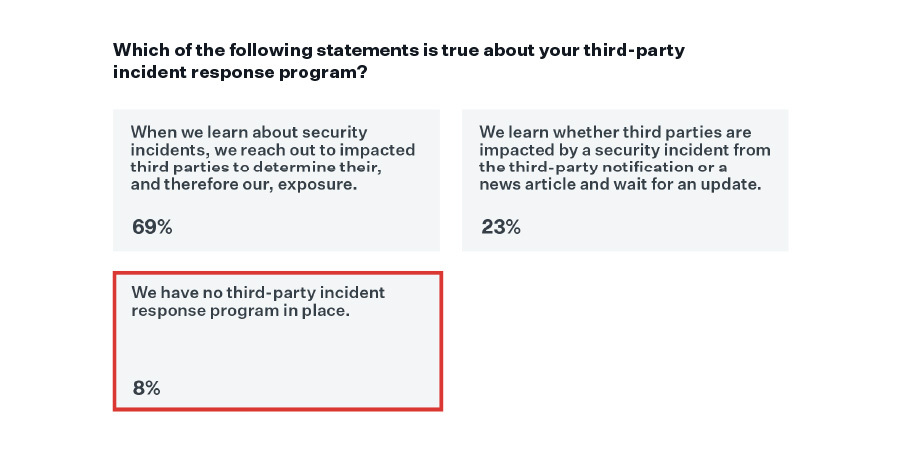
The most discouraging stats of all: 8% of companies don’t have a third-party incident response program in place at all, while 23% take a passive approach to third-party incident response. Good luck when the next SolarWinds hits.
The result: It takes about 2.5 weeks between incident discovery and remediation – a lifetime for an organization to be vulnerable to a potential exploit.
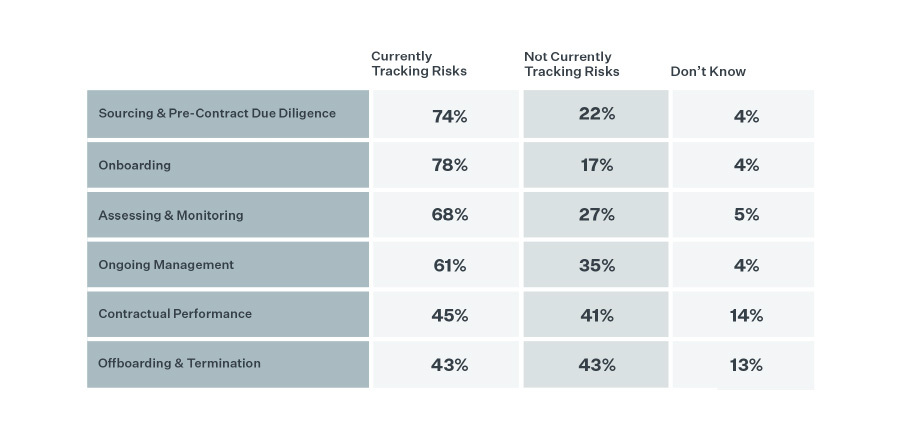
Fewer Than Half of Companies Are Tracking Risks in Later Stages of the Vendor Lifecycle
Contractual risks and risks at the offboarding and termination stage of the relationship don’t rank very high among the risks companies currently track – 45% and 43%, respectively. In fact, the percentage of customers tracking risks declines as the relationship lifecycle matures, indicating that companies are focused more on risks at the earliest stages, less so as the relationship continues. With all the risk involved in missing contractual expectations, this is surprising.
3 Best Practices Recommendations to Improve Your TPRM Roadmap
The results of this study demonstrate that TPRM teams are making progress toward a more strategic approach to TPRM, but three areas require additional improvements.
1. Expand Assessments Beyond IT Security to Unify Teams Under a Single Solution and Simplify Audits
Looking at third-party risk solely through an IT lens will miss important risks. Therefore, invest in a solution that includes built-in questionnaire templates and complementary intelligence to address areas including everything from business/operational, reputational and financial risks to ESG and compliance risks.
By unifying non-IT risk intelligence with the results of traditional cybersecurity and data privacy assessments, you can:
- Enrich visibility into supplier risks while meeting the needs of multiple departments
- Elevate the strategic value of your third-party risk management program
- Improve reporting and eliminate the persistent use of spreadsheets to collect and analyze third-party risk data
In addition, considering that nearly a third of companies say it takes more than 30 days (and some more than 90 days) to produce the evidence required to meet regulatory audits, collecting these insights in a single platform will accelerate audit reviews and enable to teams to get back to their day jobs.
2. Automate Incident Response to Reduce Cost and Time
With 45% of companies reporting a security incident in the last year – and 69% of companies saying it’s their priority – more work needs to be done to automate incident response to mitigate results. Invest in mature tools and processes that:
- Centrally manage all vendors in a single platform – gaining visibility into your third-party ecosystem is the first and most important step
- Know which third parties (and Nth parties) are at risk from a breach by mapping supplier relationships based on technology usage
- Ask the right questions of the right vendors with contextual event assessment questionnaires
- Get early warning of incidents by enabling vendors to proactively submit event assessments
- Reveal potential impacts by continuously tracking, scoring and managing cyber, business, reputational, and financial risks in a single platform
- Quickly mitigate risks to your business with access to prescriptive remediation guidance
- Satisfy the needs of regulators, board members, and other stakeholders with proactive reports on incident response progress and mitigations
3. Close the Loop on the Third-Party Lifecycle
Data from this year’s study shows that risk assessment discipline trails off as the vendor lifecycle progresses. Here are a few tips for addressing risks later in the relationship.
- Contractual and SLA Performance: As you identify and address third-party risks, it’s important to keep track of all activities for each vendor and supplier. Therefore, look for a TPRM platform with strong contract lifecycle management capabilities. This is not only critical to internal reporting, but also can be a valuable tool in measuring adherence to agreed-upon terms, SLAs, KPI targets and compliance requirements. The results can inform ongoing negotiations with your business partners and ensure stronger, long-term business relationships.
- Offboarding and Termination: Offboarding is often overlooked when it comes to third-party risk management, however a lot can happen in the last days of a vendor relationship. Conducting a final risk assessment can validate that your systems and data are securely decommissioned, while also providing records for demonstrating compliance with data privacy mandates.
The 2023 TPRM Study Infographic
Review key statistics from our study of organizations trying to chart a course to TPRM success.

Take the Next Steps Toward the Right TPRM Course
Download the full e-book and infographic for additional statistics, context and recommendations to benchmark your existing TPRM practices. Then, request a demo for a strategy session with a TPRM expert.
-

2023 Gartner® Market Guide for Supplier Risk Management Solutions Cites...
Prevalent believes it is differentiated by delivering comprehensive coverage of multiple risk types and by delivering...
12/12/2023
-

Prevalent Named a Leader in the 2023 SPARK Matrix™ for...
Leading industry analyst firm recognizes Prevalent for sophisticated Vendor Risk Management offerings.
11/06/2023
-

2023 Third-Party Risk Management Study: Warning! Turbulence Ahead
Please return your seat backs and tray tables to their full upright positions and follow these...
05/09/2023
-
Ready for a demo?
- Schedule a free personalized solution demonstration to see if Prevalent is a fit for you.
- Request a Demo




