How Vendor Threat Monitoring Deciphers Data Security Risks

It is difficult to predict when or where data breaches will occur, but by utilizing a continuous cyber and business risk monitoring platform, you can gain greater visibility into potential red flags that can indicate data security issues. Red flags can include business risk events that may result in a higher likelihood of an insider threat, events indicative of higher risk industries, and lags in reporting data breaches to customers and the public. If missed, these red flags can all negatively impact data security. In this blog I will briefly review these risks and discuss how Prevalent Vendor Threat Monitoring (or VTM) can help reveal, interpret, and alleviate the risk.
The Insider Threat and High-Risk Industries
Verizon’s 2019 Data Breach Investigations Report shows that insider threats, including deliberate threats or human errors, are on the rise. Paying attention to brand risk events that affect the company’s reputation – like sexual harassment claims or discrimination lawsuits – can be potential red flags for insider threats. Financial and regulatory risk events detailing current or ex-employees committing financial crimes and facing regulatory action can also negatively affect data security because financial negligence can leave openings for hackers to exploit. Additionally, operational business risk events like unexpected layoffs or high turnover could indicate an insider threat is more likely to occur.
As well, certain industries may have inherently higher data risk. Verizon’s latest Insider Threat Report stated that Healthcare and Social Assistance and Public Administration were the industries most affected by insider and privileged misuse.
Gaining Visibility into Vendor Cyber Risks: Data Risk at a Glance
Prevalent’s VTM cyber and business monitoring solution. The first way is to group vendors, which can show trends for certain industries or companies. Users can customize vendors through tagging and grouping.
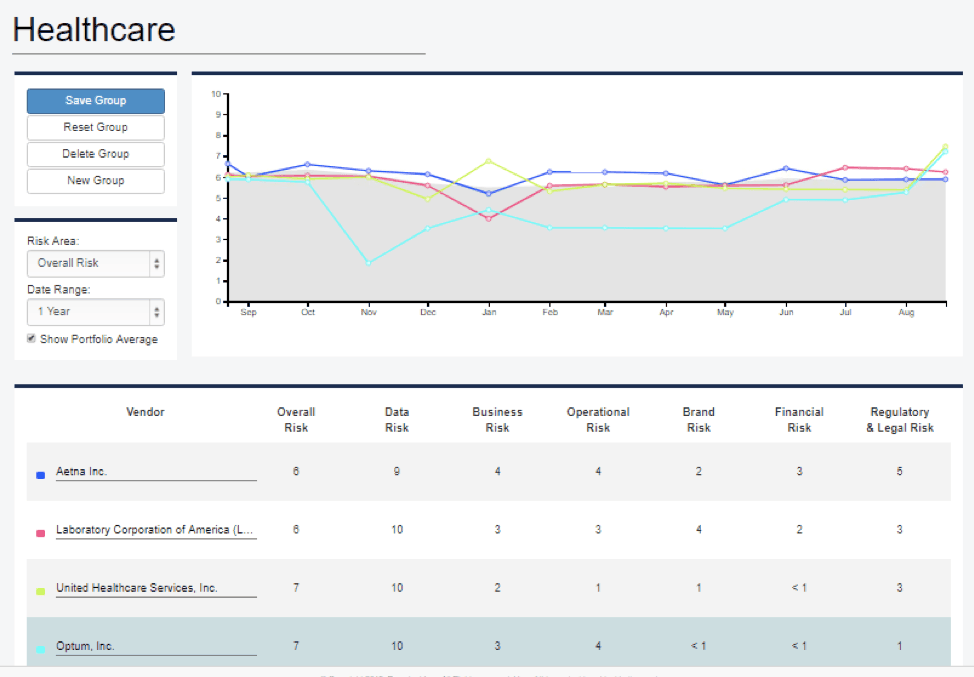
Prevalent Vendor Threat Monitoring: Vendor Grouping
Users can also look at an individual vendor’s monitoring report to see a graph of “risk trends” comparing the vendor’s overall risk in red and the industry risk as a whole in blue. By grouping third parties by industry and setting up notifications to send updates on data and business risk events, users can leverage this information in their own business decisions and in conversations with vendors.
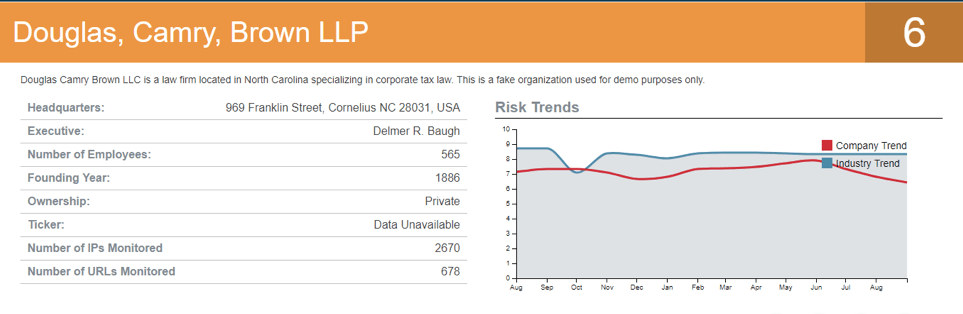
Prevalent Vendor Threat Monitoring: Vendor Risk Report
Users can also examine Prevalent’s data risk section for each vendor. Prevalent’s collection of historic data breaches in VTM can provide crucial context such as a vendor’s total number of breaches, a display of historical data breach data, and the number of records impacted over time. With this data, users can keep an eye out for clusters of past breaches to indicate potential data security problems, helping to inform their vendor assessment questionnaires. Users should also notice changes in threat-event based risk scores and events like IP threats and phishing events. A scoring change from low to medium or medium to high risk could signify data security red flags.
Third-Party Risk Management in Context
The circumstances around data breach reporting are also important. By utilizing the data breach incident details on the platform, users can gain crucial data breach context. If the vendor reported a data breach months or years after they learned of the breach, that may indicate a lack of transparency around future breaches. Without transparent and timely notification of a breach, a user may not be able to mitigate the damage caused by the breach.
For example, in 2016 Yahoo disclosed a massive data breach that occurred in 2014 and compromised the information of 500 million users. Yahoo reportedly began its internal investigation in 2014. Additionally, in 2017 Uber disclosed the 2016 hack of user and driver records through a third-party. Those with compromised records were unable to take steps to mitigate the damage during the lull in reporting. Prevalent’s platform offers analyst commentary, which can put these delays and breaches in context, and informs users about how responsive their vendors are to malicious activity. Armed with this information, users can better utilize VTM to make more informed business decisions and better select and monitor vendors.
Prevalent offers a comprehensive approach to provide visibility into the third-party risks that would have led to such data breaches. More specifically, Prevalent Vendor Threat Monitoring looks at various Transport Layer Security/Secure Sockets Layer, Domain Name System, and Application Security configuration best practices to gain insights into the security posture and maturity of an organization, while notifications can be tailored to configuration-based risk events to track when a vendor remediates an issue. The results of these risk analyses can then trigger a more complete assessment performed by the Prevalent Third-Party Risk Management Platform.
As the industry’s only purpose-built, unified solution, the Prevalent TPRM Platform combines automated assessments, continuous monitoring, and evidence sharing for collaboration between enterprises and vendors in addition to expert advisory and consulting services to accelerate vendor risk mitigation efforts. For more on the value of a 360-degree view into vendor risks, watch a demo or contact us today.
-

Reputational Risk Management in Third-Party Relationships
Learn how to manage third-party reputational risks effectively to protect your organization's brand, ensure operational resilience...
12/05/2024
-

NIST Privacy Framework for Third-Party Risk Management
Learn how integrating the NIST Privacy Framework with third-party risk management (TPRM) helps organizations enhance data...
09/12/2024
-

Third-Party Risk Management for Mergers, Acquisitions, and Divestitures
Explore best practices for managing third-party risk during business transitions such as mergers, acquisitions, and divestitures...
07/22/2024
-
Ready for a demo?
- Schedule a free personalized solution demonstration to see if Prevalent is a fit for you.
- Request a Demo



