Bonobos Breach: How to Ensure Your Third-Party CSP Is Securing Your Data

When the Cloud was invented, many of us thought it could be the “be-all and end-all” secure data center. However, as the cold reality of data breaches has taught us, moving your company’s assets, processing power and storage to a third-party cloud environment doesn’t relieve you of your responsibility to understand where and how your data is secured.
Bonobos, a Walmart subsidiary, is the latest example. The company recently reported a data breach at a third-party cloud service provider (CSP) that resulted in customer PII exposure. This breach is another illustration of the pitfalls of shared responsibility. Is it on the customer, the third party, or the CSP?
Understanding Cloud Service Provider Responsibility
Understanding the differences between cloud service levels can help you determine which control standards to embed into your cloud computing service models. There are four basic cloud service provider (CSP) levels:
- Enterprise IT (on prem)
- Infrastructure as a Service (IaaS)
- Platform as a Service (PaaS)
- Software as a Service (SaaS)
Each level of support reflects whether risk responsibility lies with the customer or the provider. Under the Enterprise IT structure, the provider has controls in place for all ten responsibility zones (see table below). However, if you engage in any flavor of “as a Service,” then the responsibility can vary between the customer, the provider, or both.
When you assess supply chain security, beware of blanket responses from your vendors indicating that they are “protected” in the cloud. If they use the cloud, then determine which level of service they have and what controls are in place to support what’s covered in their CSP contract.
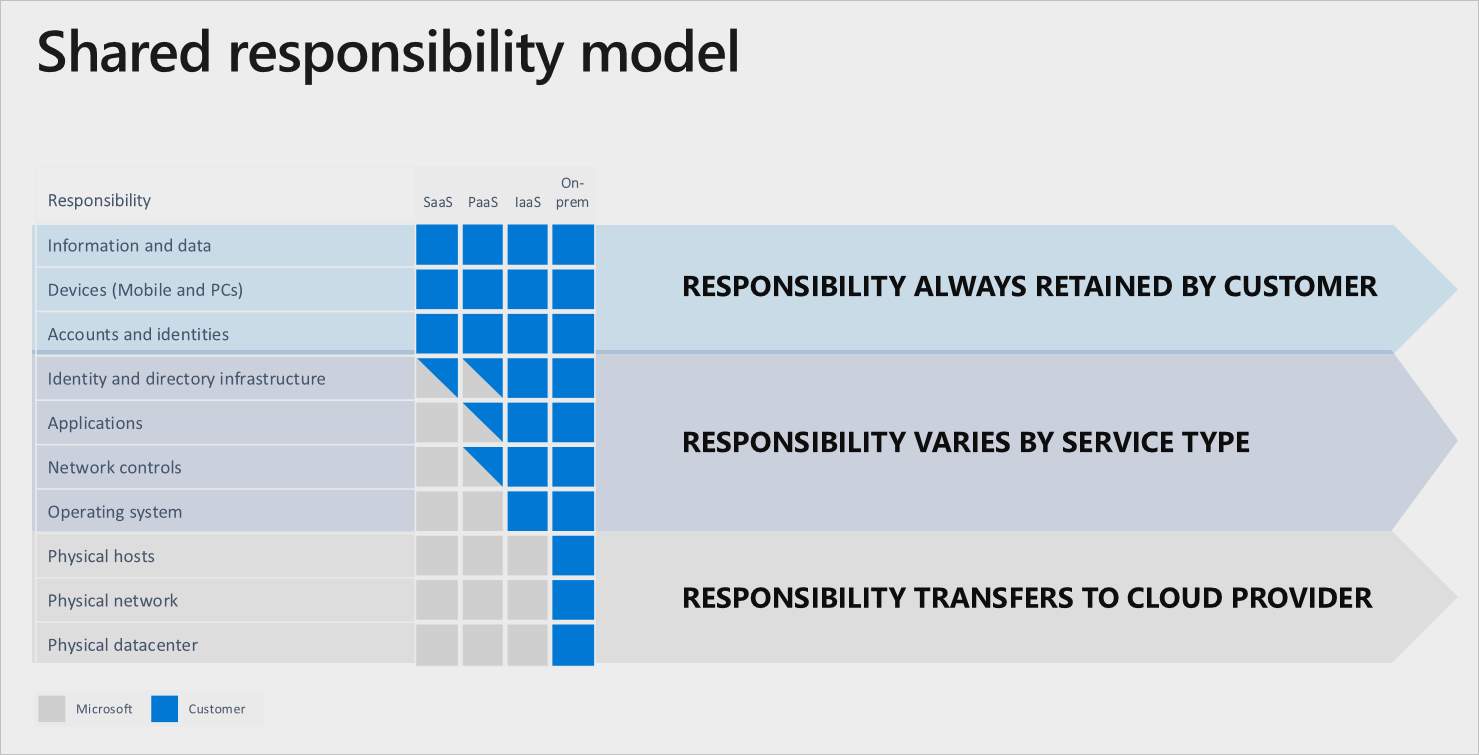
Microsoft’s Shared Responsibility Model*
Assessing Your Third-Party Cloud Service Provider Risks
Breaches like the one affecting Bonobos serve as a reminder to implement best practices, embed control standards to protect your data, and continuously assess third parties that store and manage your data. Whether you are using cloud services for backup data or active data, be sure to consider the following best practices:
- Keep up to date on evolving security practices
- Remember to use authentication, authorize with proper identity management, and maintain accountability with log management
- Store privileged credentials securely and safeguard the keys
- Implement and use hardening guides
- Place a focus on change management
- Utilize automated checking
- Regularly assess the security posture of your vendors, and validate the presence of controls with continuous monitoring
Prevalent can assist with security evaluations of IaaS, PaaS, SaaS and other CSPs by using the built-in Cloud Security Alliance (CSA) Consensus Assessments Initiative Questionnaire (CAIQ) questionnaire in the Prevalent Platform. This questionnaire is an industry standard for documenting cloud security controls and CSP security capabilities using standardized, best-practice terminology. With comprehensive reporting against the standard, you gain a clear picture of your CSP’s security controls and can make better-informed decisions.
To complement the regular controls assessment, Prevalent Vendor Threat Monitor can deliver continuous cybersecurity, reputation and financial insights into your CSPs. This includes monitoring for hacker chatter on dark web forums, which provides a window into real and potentially unseen risks, while also validating the presence of certain controls.
Handing control and management of your data to a CSP does not necessarily mean that you are free of responsibility for regulatory governance and accountability. So, when a supplier or vendor indicates they are using cloud services, do not stop your assessment there. Find out what CSP level your third party is using and how controls are governed on both the vendor and the provider sides of the house. Also, be sure to consider active, backed-up, and terminated databases where applicable. It might save you from a world of heartache!
Next Steps
For more on how Prevalent can help address the regulatory and governance aspects of third-party risk management for CSPs, check out our best practices white paper, The Third-Party Risk Management Compliance Handbook. Or contact us for a strategy session today.
*Source: Lanfear, Terry. “Shared Responsibility in the Cloud” Microsoft Azure Documentation, 16 Oct. 2019
-

The Top 7 TPRM Predictions for 2025
2025 promises to be a consequential year for third-party risk management. Read our top TPRM predictions...
12/12/2024
-

Developing a Third-Party Risk Management Policy: Best Practice Guide
Learn how a third-party risk management (TPRM) policy can protect your organization from vendor-related risks.
11/08/2024
-

Vendor Offboarding: A Checklist for Reducing Risk and Simplifying the...
Follow these 7 steps for more secure and efficient offboarding when third-party relationships are terminated.
10/17/2024
-
Ready for a demo?
- Schedule a free personalized solution demonstration to see if Prevalent is a fit for you.
- Request a Demo




