2022 Verizon Data Breach Investigations Report: How to Respond to Growing Third-Party Vendor and Supply Chain Attacks

The 2022 Verizon Data Breach Investigations Report contains a veritable treasure trove of data analyzing more than 23,896 security incidents and 5,212 breaches for the time period between November 1, 2020 and October 31, 2021. However, some disturbing trends in the data should alert security, risk, and vendor management teams to better prepare for future incidents. Here are the key third-party risk management takeaways from the report.
62% of System Intrusion Incidents Came Through a Partner
Every organization relies on third parties to some degree – whether vendors providing goods or services to support the business or suppliers producing inputs for final products. The Verizon data shows that partners (e.g., third parties, vendors, or suppliers) accounted for 62% of system intrusion incidents in the last year (see Figure 36 from the report). When you consider that partners were involved in just 39% of data breaches in 2008, you’ll quickly see the astonishing growth over time of third parties involved in security incidents. For every third party you do business with, your attack surface expands exponentially.
Software supply chain attacks (via software updates) are driving much of the growth in partner-led intrusions, with these types of incidents accounting for 9% of total incidents in 2021. A single compromised software provider pushing updates out to thousands of its customers (that, in turn, might work with thousands of vendors, suppliers and other third partiers – i.e., secondary victims) can wreak untold havoc (read: SolarWinds).
Although the dataset showed that third-party breaches represent just 1% of breach data, Verizon notes that in that method, stolen credentials and ransomware were two of the top five action varieties. This means third-party risk practitioners should be actively ensuring that their third-party vendors and suppliers have strong password policies and network segmentation architectures in place – and be able to independently validate those practices.
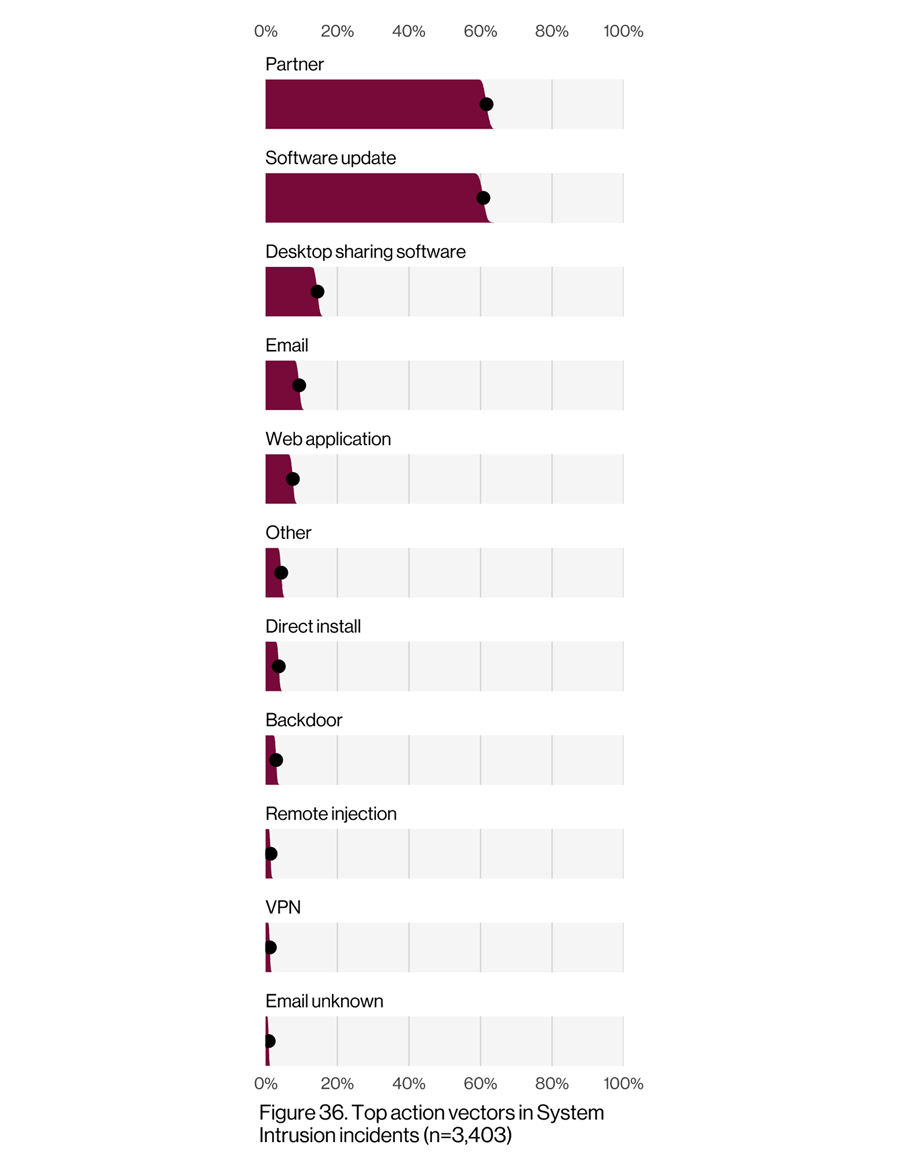
(Source: Verizon Data Breach Investigations Report, May 2022)
Manufacturing Industry Is a Growing Target
From an industry perspective, partners represent 1% of threat actors in Manufacturing. While 1% might not seem like a high number, consider the damage caused by a single system intrusion event such as the ransomware attack on Toyota supplier Kojima industries. Although outside the window of this dataset, such a breach should serve as a reminder that one incident can have wide and long-lasting impacts. In fact, the Verizon data shows that the Manufacturing industry as a whole is a growing target – with system intrusions growing exponentially. See Figure 92 from the report.
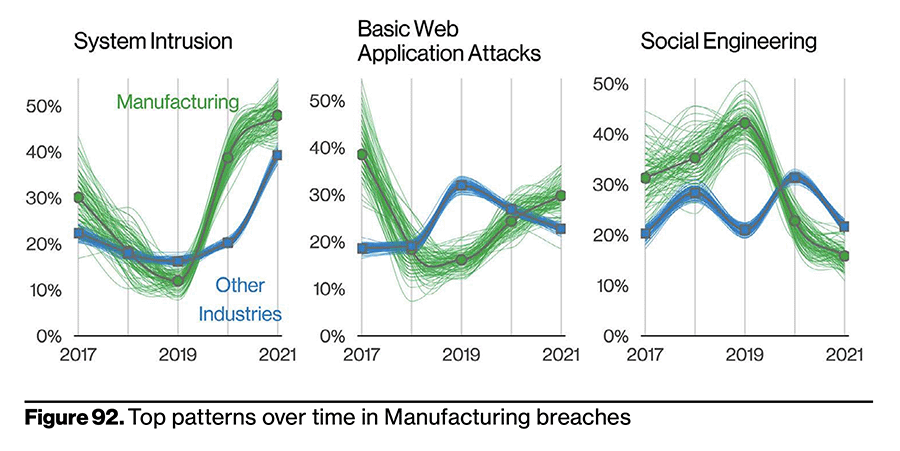
(Source: Verizon Data Breach Investigations Report, May 2022)
Significant Increase in Ransomware
Continuing the ransomware theme, ransomware breaches increased 13% over 2020, which according to Verizon was a greater year-over-year increase than the past five years combined. See Figure 38 from the report below.
The increase in incidents and breaches shouldn’t come as a surprise; you only have to read the headlines to learn of the latest victim. The last year has featured significant third-party ransomware breaches including PracticeMax, Kaseya, and Colonial Pipeline – many of them variants of the Ryuk ransomware.
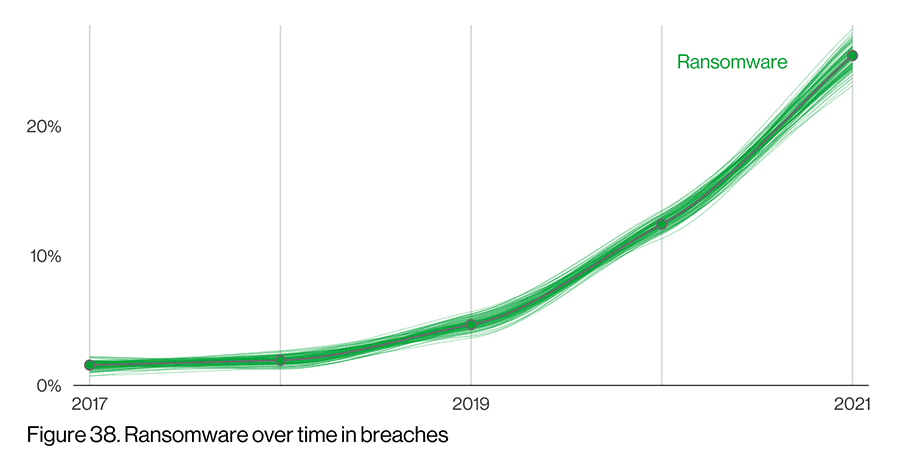
(Source: Verizon Data Breach Investigations Report, May 2022)
Seven Battle-Tested Best Practices to Reducing Third-Party Risk
With increasing numbers of third-party breaches and ransomware attacks organizations using manual methods to manage third-party vendor and supplier risks should consider implementing the following best practices to speed identification, triage and mitigation.
- Start managing third-party risk before the contract is signed by analyzing recent data breaches and regulatory actions, and uncovering potentially risky fourth-party relationships – data that can further inform your vendor selection decisions.
- Build incident and breach response times into vendor contracts, and automate reporting against enforceable SLAs to trigger alerts when expectations are missed. Additionally, ensure your vendors have easy, intuitive mechanisms for reporting and informing of incidents and breaches.
- Measure the inherent risk from third-party vendors, and tier suppliers according to their inherent risk scores to scope ongoing due diligence assessments after onboarding.
- Conduct detailed internal controls-based vendor risk assessments against best practices security frameworks such as NIST or ISO, and build workflows and reporting to escalate control exceptions and suggest remediations. These activities should account for specific risk domains including human factors, data management, and authentication mechanisms.
- Validate the ongoing effectiveness of a vendor’s controls by correlating externally observable cybersecurity metrics with the results of internal controls assessments. For example, if a vendor’s user IDs and passwords are discovered for sale on a Dark Web forum, then you can link that finding to the assessment answer discussing the strength of their password policy and determine if changes must be made.
- Identify relationships between the organization and third parties to discover dependencies and visualize information paths that could be open to fourth-party attack.
- Leverage workflows to report on system access, data destruction, and access management to close potential pathways into your organization once a vendor is offboarded.
How to Handle Third-Party Vendor and Supplier Security Incidents
As vendor data breaches and supply chain disruptions continue to make headlines, it’s easy to become overwhelmed by the demands of assessing risk across hundreds (or even thousands) of third parties.
To help your team be more proactive in identifying and mitigating third-party security incidents, Prevalent has developed an incident response checklist based on the NIST Computer Security Incident Handling Guide, SP 800-61. The checklist prescribes four foundational phases that security teams should consider for their incident response programs. Use this checklist, along with the complete NIST guidance, to compare your existing third-party incident response processes against best practices.
Then, request a Prevalent demo for a customized strategy discussion on how to automate your TPRM program from vendor selection to offboarding.
-

61% of Companies Have Been Breached by a Third Party...
Read the findings from our annual TPRM study and implement these best practices to put out...
05/08/2024
-

2023 Gartner® Market Guide for Supplier Risk Management Solutions Cites...
Prevalent believes it is differentiated by delivering comprehensive coverage of multiple risk types and by delivering...
12/12/2023
-

Prevalent Named a Leader in the 2023 SPARK Matrix™ for...
Leading industry analyst firm recognizes Prevalent for sophisticated Vendor Risk Management offerings.
11/06/2023
-
Ready for a demo?
- Schedule a free personalized solution demonstration to see if Prevalent is a fit for you.
- Request a Demo




