Latest Analyst Report: The 2023 Gartner® Market Guide for Supplier Risk Management Solutions
Why Should You Care About Your Vendors’ Business Risk?
Vendors who have access to your networks offer potential weaknesses to your firm’s information security. Although there are ever-increasing opportunities for employees to make costly information security mistakes, companies’ have limited resources to deal with these external risks, thereby increasing their attack surface. And while it might seem more obvious to monitor the cyber risks your partners expose you to, it is easy for CISOs and Third-Party Risk teams to overlook important changes in their vendors’ business risk landscapes.
Why business risks are worth monitoring
Seemingly innocuous business changes such as acquisitions, layoffs, scandals and significant financial shortfalls can lead to major data losses for your firm. Mergers and acquisitions can be distracting and lead to a temporary loss of governance or oversight during the business combination process. Mass layoffs can lead to data security risks from insider threats or mistakes made during personnel turnover. Scandals can make firms a target for phishing attempts and hacktivism. A vendor’s ongoing financial difficulties can indicate a decrease in information security investment. By monitoring these business risks as they occur, CISOs and IT teams can anticipate and better mitigate potential data risk threats before they impact your firm’s operations.
The Orbitz use case
These concerns are not academic; the Orbitz breach reported in March 2018 is a real example of how a vendor’s acquisition had disastrous effects for American Express. Expedia, an American Express vendor, acquired Orbitz in 2015. During the acquisition, a legacy Orbitz platform was left active without being integrated into Expedia’s more up to date and better-secured platforms. Hackers used this legacy platform to access 880,000 American Express credit card numbers. With proper business risk monitoring, American Express would have been notified of the merger and could have taken steps to mitigate this risk, such as requesting an updated assessment from Expedia.
Business risk monitoring is only one tool at the disposal of Third-Party Risk teams. Using business risk monitoring, vendor assessments and continuous data risk monitoring together is a powerful combination that gives firms customized and actionable intelligence on potential threats and weaknesses from all angles. For a consolidated view of what this looks like, see the screenshot below.
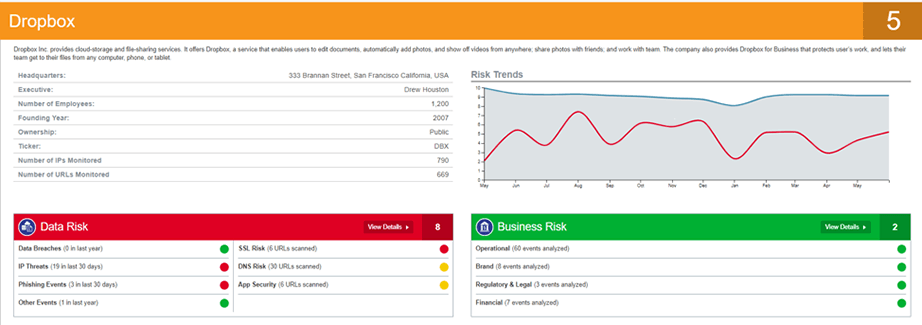
In fact, Prevalent is the only solution that offers both continuous data and business risk monitoring. By coupling monitoring of data risks with forward-looking monitoring of operational, legal, financial, and brand-related threats, Prevalent provides our clients with the most proactive set of solutions needed to navigate their third-party risk. Then, you can layer this information on to the results of your deep internal controls-based assessments for what amounts to a 360-degree view of your vendor risks.
Want to see this in action? For more on our vendor threat monitoring solution, contact us today.
-

Why Third-Party Monitoring Should Include Cyber and Business Risks
Business challenges, financial concerns, and reputational issues can often predict potential security risks. Learn how to...
04/11/2024
-

How Data-Driven Third-Party Risk Management Can Mitigate Ransomware Risks
This use case illustrates the value of combined internal controls assessment data and external third-party risk...
04/08/2024
-

The Third-Party Vendor Risk Management Lifecycle: The Definitive Guide
Your organization encounters distinct risks at each step of the vendor relationship, making it important to...
03/07/2024
-
Ready for a demo?
- Schedule a free personalized solution demonstration to see if Prevalent is a fit for you.
- Request a Demo



