Five Steps to Supply Chain Resilience

Supply chain challenges have been a prominent topic in the news recently. Notable incidents include SolarWinds data breach, the Colonial Pipeline ransomware attack, and the global chip shortage. As a result, improving supply chain resilience and reducing supply chain risk have become prime concerns for many organizations, from Fortune 500 to small and mid-sized businesses.
Risk managers have a difficult task ahead. Today's supply chains are incredibly complex, and for larger organizations they can can consist of thousands of third, fourth and Nth party vendors. Unfortunately, many organizations lack sufficient visibility into their own vendors, much less vendors of their vendors.
This article highlights the value of supply chain resilience and introduces five steps you can take to reduce the risk of suffering a catastrophic supply chain failure. If you are interested in learning more about how to build a robust supply chain risk management program, check out our article on managing SCRM risk.
Why Is Supply Chain Resilience Important?
Supply chains have become incredibly complex in the past two decades, as globalization has spread. As a result, many organizations lack visibility into their extended supply chains, which can prove to be incredibly detrimental. For example, key decision makers at organizations ultimately affected by the Kaseya breach may have been unaware that their MSPs were using Kaseya's solution in the first place. Issues like this can lead to costly delays when data breaches and other security incidents arise.
Furthermore, supply chain attacks are gaining in frequency. Attacks are now targeting pivotal elements of the global supply chain, such as gas pipelines and meat processing plants. Attackers have discovered that by compromising critical supply chain bottlenecks, they can extort large ransomware payments with little hassle.
It is now more important than ever to take proactive steps to improve your supply chain resilience, protect yourself from supplier-driven cyberattacks, and understand the level of risk your organization faces.
What Are the Key Elements of Building a Resilient Supply Chain?
The truth is that building a robust and resilient supply chain is difficult. You have to manage internal stakeholders who have preferred vendors, as well as hundreds to thousands of external vendors, many of which may pose unacceptable risks to your organization. Below are steps you can take to understand and mitigate risks as part of a supply chain resilience plan.
Step One: Centralize and Monitor your Suppliers
Gaining visibility into your supply chain is critical. Many organizations are entirely unaware of which vendors they are working with due to siloed departmental structures and lack of organization. Therefore, the first and most important step is to centralize supplier data in a single place where you can keep track of vendors, risk profiles, and contracts.
Centralizing vendor data also enables your team to quickly and efficiently identify vendors with high profiled risk. Vendor data centralization enables a single point of reference for vendor relationships; it helps you to easily keep track of contract status, potential disruptions, and potential changes in inherent or profiled risk in near-real-time.
In addition to monitoring vendors, you also need to monitor how your supply chain is functioning in real-time. Be sure to implement a system to track incoming and outgoing shipments, contract performance, and other critical vendor data. This can help alert you to any early issues that may cause disruptions later on.
Step Two: Identify Mission-Critical Suppliers and Map Dependencies
Supply chain resilience is largely dependent on identifying vendors that are most critical to your organization and then reducing risk to an acceptable residual level. Which vendors are critical will vary by industry. For instance, manufacturing companies are far more at risk of raw material disruptions than software companies. A software-as-a-service company may be entirely reliant on a cloud services provider such as AWS or Azure, but also be dependent on an outsourced hiring firm. When planning how to reduce risk, they would be best served to focus not only on failover sites and backups for the data, but also on ensuring they have a backup process in place to hire talent.
During this stage, it is also crucial to map dependencies and understand vendors of vendors. Map data flows and dependencies between vendors to visualize third-party dependencies. Third-Party Risk Management platforms often have built-in functionality for easy dependency mapping. However you can also gather dependency data as part of a third-party risk questionnaire and manually chart supply chain relationships.
Other risks can be much more centralized. Auto manufacturers are currently suffering from an acute chip shortage due to COVID-related manufacturing shutdowns in China in 2020. This has proven disastrous as even a small uptick in COVID cases in a handful of countries can result in chip shortages that percolate through the economy and lead to extreme price inflation for new and used vehicles.
Identifying the suppliers that your business can’t function without is a critical step to building towards supply chain resilience. When you understand your critical vendors, you then need to do a deep dive and understand your vendors' supply chains. Gathering this intelligence can alert you to issues that may prevent your third party from performing in the future, while also enabling you to further understand your supply chain risk posture.
As part of getting visibility into your supply chain and extended supply chain, consider tiering your vendors based on business criticality. Tiering involves first understanding a vendor's profiled risk, and then creating vendor tiers based on their importance to the business. This can help determine appropriate controls to put into place as well as focus your risk reduction efforts on the most critical vendors.
Step Three: Avoid Concentration Risks
Having a diverse supply chain ecosystem can result in far more redundancy and reduced risk. When onboarding new suppliers, consider both geographic risk and fourth-party risk. Are multiple suppliers reliant on the same high-risk third-party vendor? Are your suppliers concentrated in one geographic area?
The more geographically diverse your supply chain ecosystem is, the better. Natural disasters can quickly cripple an organization if multiple mission critical vendors are affected. Likewise, if any of your third-parties are reliant on a single fourth party, a single disaster, financial incident, or legal problem could spell trouble for your supply chain.
When onboarding new suppliers it’s worth considering the following:
Is your supplier critical to business operations?
Could the supplier be easily replaced in the event of a disruption to their business or their third parties?
Are they reliant on the same third-party suppliers as other third parties you work with?
Would contracting with them increase your supply chain resilience or reduce it?
Do you have visibility into their third and fourth party risk?
Step Four: Understand Your Risk
Once you have identified critical vendors, and you have visibility into your immediate supply chain, you need to begin working to understand your risk. Applying a vendor risk matrix can help quickly identify vendors that pose significant risks to your organization. A vendor risk matrix can enable your organization to numerically and uniformly score vendors based on a variety of risks, taking out much guesswork and subjective interpretation. Risks are categorized based on likelihood and severity, allowing you to focus efforts on risks that are both likely and substantial.
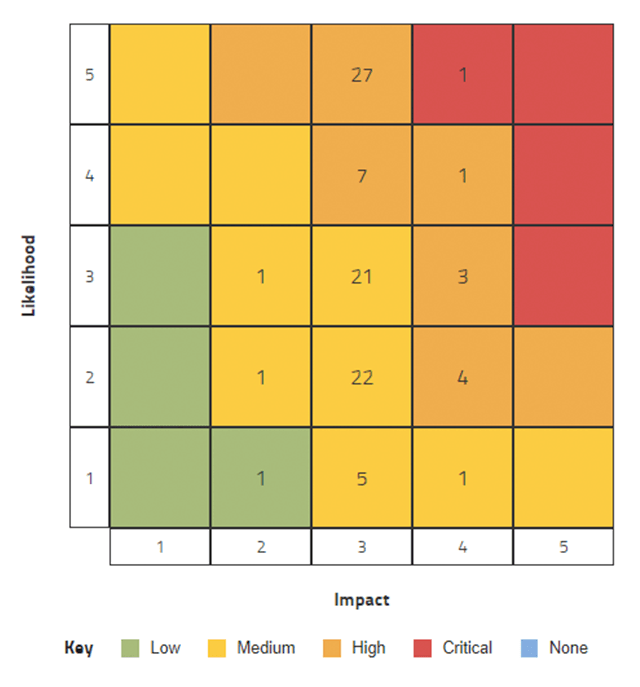
Utilizing a vendor risk matrix lends consistency to supplier comparisons during the sourcing and selection process.
When evaluating risk you can also perform core assessments against industry standards and frameworks. For example, if you are considering onboarding a vendor that will be handling large amounts of sensitive data, it may make sense to assess their compliance with the NIST Cybersecurity Framework or ISO 27001.
Data and security isn’t the whole picture either. You also need to be concerned with reputational and financial risks. If any organization is utilizing slave labor in its supply chain, then you run serious ethical and public relations risks. Other ESG risks include environmental destruction, bribery, corruption, and other risks related to unsavory business practices tarnishing your organization's reputation.
It is also crucial that you screen suppliers for financial risks, particularly if they have high profiled risk. If your organization is highly dependent on a vendor with poor financial structure and performance, a sudden bankruptcy or disruption could quickly derail your supply chain.
Quick Tip: When evaluating vendors to assess your supply chain resilience, make sure to consider not just third-party vendors, but fourth and Nth parties as well. A vendor may look rock solid with a low-risk profile, but if they are reliant on risky third parties themselves, they may pose substantial risk.
Free Vendor Risk Report
Get a complimentary Prevalent Vendor Threat Monitor (VTM) report for a third party of your choice. You’ll get an “outside-in” view of exposures and threats from hundreds of thousands of public and private sources.

Step Five: Focus on High-Risk Vendors
Some vendors may have low profiled risk, but still represent a substantial level of inherent risk. For example, if you work with an HVAC company that regularly has access to your internal IT environments, then the risk can be substantial. While on the surface an HVAC vendor would appear to have an extremely low risk level, it’s important not to overlook their access and the services they provide.
A delay in an HVAC installation may not endanger your organization, but that HVAC vendor introducing malware onto your credit card processing system poses an extremely high degree of risk. This risk could be mitigated by carefully regulating their access to IT equipment, employing the principle of least privilege, and ensuring that vendors are effectively offboarded and credentials revoked upon completion of the contract.
Other high-risk vendors will be more obvious. To return to the SaaS company example, a cloud service provider could make or break a growing software company. As such, it makes sense for the software company to engage in serious risk mitigation strategies such as employing offsite backups, and extensive planning in the event of a prolonged outage. When mitigating risk, your goal should be to reduce the risk and improve supply chain resilience by employing mitigation strategies and reducing risk to an acceptable residual level.
Bonus Step: Practice Continuous Improvement
Building a resilient supply chain is not a one-and-done process. You need to focus on continuous improvements in both understanding the risk that suppliers pose, and also continuously improve your mitigation strategies. As you build towards a full third-party risk management program, you will want to employ tiered vendor risk assessment questionnaires and potentially move towards a third-party risk management software solution.
Final Thoughts on Supply Chain Resilience
Successfully implementing supply chain resilience enables your organization to outperform your competitors when risks arise that affect the overall market. Investing in risk management systems for the supply chain offers many benefits. Organizations that prioritize developing and implementing a risk management strategy for their supply chains are more likely to reduce their risk than those that do not.
Companies that implement risk management strategies in their supply chains see a clear competitive advantage compared to others in their industry. Organizations that apply the power of a dedicated third-party risk management platform to their risk mitigation strategies benefit even more.
Take the Next Step Toward Building a More Resilient Supply Chain
Wondering how to get started? Learn more about our solutions for supply chain resilience, or check out our on-demand webinar: Supply Chain Risk: Fourth Parties and Beyond. Interested in whether Prevalent’s solutions and services may be a fit for your organization? Request a demo.
-

Developing a Third-Party Risk Management Policy: Best Practice Guide
Learn how a third-party risk management (TPRM) policy can protect your organization from vendor-related risks.
11/08/2024
-

Vendor Offboarding: A Checklist for Reducing Risk and Simplifying the...
Follow these 7 steps for more secure and efficient offboarding when third-party relationships are terminated.
10/17/2024
-

Third-Party Risk Management: The Definitive Guide
Third-Party Risk Management (TPRM) has advanced from being an annual checklist exercise to a critical daily...
10/07/2024
-
Ready for a demo?
- Schedule a free personalized solution demonstration to see if Prevalent is a fit for you.
- Request a Demo



