Latest Analyst Report: The 2023 Gartner® Market Guide for Supplier Risk Management Solutions
Third-Party Risk Management: How to Stay Off the Regulatory Radar

Editor’s Note: This is the first blog in a series entitled Third-Party Risk Management: How to Stay Off the Regulatory Radar. Each week, we will analyze a regulation, industry standard, or security framework that requires organizations to adopt a third-party risk management program to tighten IT security controls and reduce risk. We will highlight the key third-party risk management requirements and what it takes to meet regulatory compliance and keep auditors at bay.
Regardless of industry, corporate compliance and reporting is an essential part of everyday operations. Ensuring internal adherence to regulations, guidance, and industry standards is complex and challenging at best, but tack on compliance mandates related to third parties, vendors, business associates, and supply chain partners, and the burden of managing data risk takes an entirely new trajectory.
It’s clear that as cyber threats continue to grow, organizations need to do more to strengthen their defenses. That includes examining the security posture of an organization’s vendors.
An Increasingly Complex Digital Society
Thanks to modern technology and the internet, organizations today are outsourcing at a rapid pace. There are many reasons for this. A big one is to focus on core competencies and grow IP. Another is to reduce costs. Outsourcing specific functions to specialized service providers creates efficiencies, as it’s cheaper for the expert do it. This drives performance and helps companies remain relevant in fiercely competitive landscapes.
Companies are growing their “extended enterprise”, many by up to 20% in the last year. Vendors are increasingly becoming “strategic partners”, where everyone is wining, but this comes at a cost.
Third Parties Are Huge Targets for Attacks
Just pick up a newspaper or browse the latest social media sites and you’ll see that businesses big and small face high-profile data breaches. It’s happening across all industries, in all geographies. According to a recent Ponemon study, 61% of U.S. companies said they experienced a data breach caused by one of their vendors or third parties. And this isn’t going unnoticed!
In the Face of Growing Threats, Regulators are Acting
It seems like every month, new or updated legislation is enacted, focused squarely on how to combat third-party risk. Whereas traditionally we would assume this applied mainly to financial services and healthcare verticals, regulations are cutting across all markets, along with the accompanying scrutiny from auditors, demanding that organizations create a third-party risk management program to assess, monitor and manage vendor risk.
To comply with regulations and standards, organizations should adopt a third-party risk management (TPRM) program. This includes a multi-step approach where you:
- Set the rules of third-party engagement based on your organization’s risk tolerance and data security and privacy policies
- Include these rules, as well as auditing requirements, in all third-party contracts
- Evaluate third parties via risk assessments in the form of questionnaires or surveys
- Monitor third parties to verify compliance
As noted, one of the biggest requirements in each piece of legislation or standard is performing a vendor risk assessment. It’s not a nice to have, but mandatory for most legislation.
What is a Third-Party Risk Assessment?
Risk assessments provide an inside-out approach to determine vendor compliance with IT security controls and data privacy requirements, while ensuring that third parties meet the same levels of compliance as your organization. The goal of the assessment is to understand how data is being secured and to identify risk. Remediation workflows between an organization and its vendors facilitate risk management and mitigation.
While regulatory guidance varies slightly across governing authorities and standards bodies, all agree that conducting a risk assessment, with proper due diligence before and during the lifecycle of each business relationship, is a critical step to reducing third-party risks. These risk assessments are not only mandated under most regulations but can also be a key tool for organizations as they develop stronger data and privacy security measures.
You MUST Assess your Vendors!
All regulations, guidelines, and industry standards listed below require the use of internal, control-based third-party risk assessments. While outside-in risk scoring or ranking can deliver risk insights, it will not meet compliance requirements when used as the only mechanism to evaluate vendor risk. Pairing both assessments and monitoring is preferred, but at a minimum, you must assess vendors.
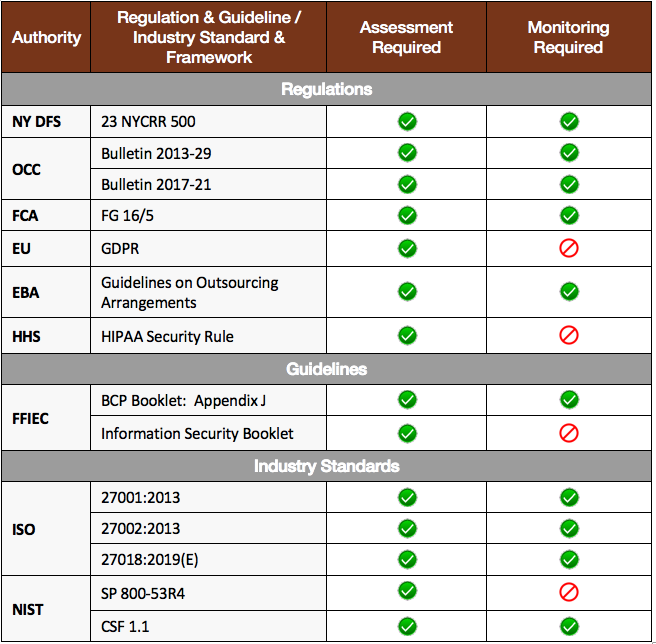
How Prevalent Solutions Address Third-Party Compliance Requirements
Prevalent offers a unified third-party risk management platform that enables you to better reveal, interpret and alleviate risk. Delivered in the simplicity of the cloud, the Prevalent platform combines automated vendor assessment with continuous threat monitoring to simplify compliance, reduce security risks, and improve efficiency. Key capabilities include:
- A library of 50+ pre-defined, customizable assessment questionnaires, backed by automated capabilities for gathering and analyzing vendor data
- Bi-directional remediation workflows to facilitate risk management and mitigation, with complete audit trails for all vendor communications and risk decisions
- A central reporting console for visualizing compliance and risk status across the vendor landscape
- Unique data mapping assessments to identify where regulated data exists within an organization – both internally and with third-party vendors
- Deep data security auditing and business monitoring capabilities that allow you to move beyond tactical network health reporting to reveal critical operational, financial, legal and brand risks
With Prevalent, you gain a 360-degree view of vendor risk – both inside-out and outside-in – for managing regulatory compliance and aligning with industry standards and guidelines.
Trust Prevalent to Help You Manage Regulatory Compliance
To learn more about achieving compliance, download The Third-Party Risk Management Risk Management Compliance Handbook today. It reviews the key third-party risk management requirements in common regulatory and security frameworks, while mapping Prevalent Third-Party Risk Management capabilities to specific mandates. It’s essential reading for anyone responsible for managing supply-chain compliance initiatives.
-

How to Use SOC 2 Reports from Vendors and Suppliers
SOC 2 reports can simplify your third-party risk management program. Here are 7 FAQs to get you started!
04/10/2024
-

Meeting PCI DSS Third-Party Service Provider Requirements
All third-party service providers with access to cardholder data – including shared hosting providers – must...
04/02/2024
-

Using NIST SP 800-161 for Cybersecurity Supply Chain Risk Management
Learn about the applicable cybersecurity supply chain risk management (C-SCRM) guidelines in NIST SP 800-161r1 and...
03/26/2024
-
Ready for a demo?
- Schedule a free personalized solution demonstration to see if Prevalent is a fit for you.
- Request a Demo



