Latest Analyst Report: The 2023 Gartner® Market Guide for Supplier Risk Management Solutions
Vendor Risk Management: 8 Keys to Success

What Is Vendor Risk Management?
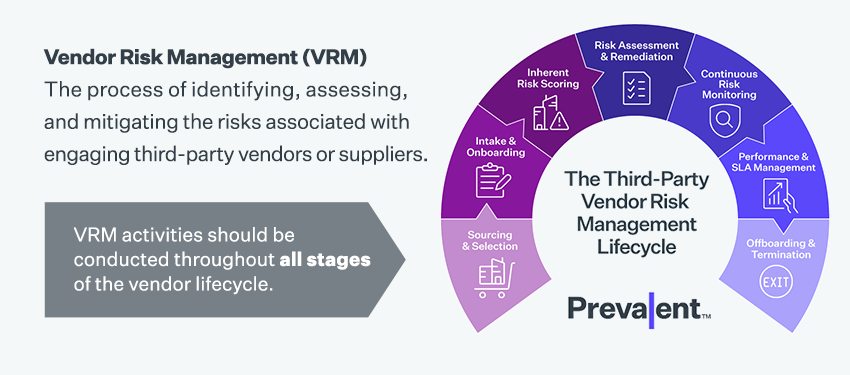
Vendor risk management (VRM) is the process of identifying, assessing, and mitigating the risks associated with engaging third-party vendors or suppliers who provide goods or services to an organization. VRM is an important aspect of enterprise risk management, as vendors can introduce risks that can negatively impact an organization's operations, reputation or compliance posture. VRM activities should be conducted throughout all stages of the vendor lifecycle, including sourcing & selection, intake & onboarding, inherent risk scoring, risk assessment & remediation, continuous risk monitoring, performance & SLA management, and offboarding & termination.
Why Is Vendor Risk Management Important?
Vendor risk management is important for several reasons, including:

Dependency on vendors
Many organizations rely on external vendors for critical services, products, or components. Any disruption or failure in the vendor's operations can directly impact the organization's ability to deliver its own products or services. Vendor risk management helps identify and mitigate potential risks associated with these dependencies.
Data security and privacy
Vendors often have access to sensitive data or systems of the organization. Inadequate security measures or data breaches at the vendor's end can lead to the compromise of valuable information, including customer data. Vendor risk management helps assess the security practices of vendors, ensuring they have robust measures in place to protect data.
Regulatory compliance
Organizations are subject to various regulatory requirements, such as data protection laws or industry-specific regulations. Vendors that handle regulated data or processes must adhere to these requirements as well. Effective vendor risk management ensures that vendors comply with relevant regulations, reducing the organization's exposure to compliance failures and associated penalties.
Business continuity and resilience
Vendors play a crucial role in maintaining business continuity. If a vendor experiences disruptions, such as natural disasters, financial instability, or operational failures, it can impact the organization's operations. Vendor risk management helps identify potential vulnerabilities and establish contingency plans to mitigate the impact of vendor-related disruptions.
Reputation and brand protection
A vendor's actions or failures can have a significant impact on an organization's reputation and brand image. For example, if a vendor is involved in unethical practices, environmental violations, or public controversies, it can reflect poorly on the organization that partnered with them. Vendor risk management helps assess the vendor's reputation, ensuring alignment with the organization's values and protecting its brand.
Cost optimization and performance
Effective vendor risk management enables organizations to assess vendors' financial stability and performance. By evaluating vendors' capabilities, organizations can make informed decisions about which vendors to engage with, negotiate favorable terms, and avoid potential financial losses or underperformance.
Overall, vendor risk management allows organizations to proactively identify and address risks associated with vendor relationships, protecting their operations, reputation, data, and compliance while optimizing costs and ensuring business continuity.
What Are the Types of Third-Party Vendor Risk?
A vendor risk management program can enable your organization to address a broad range of threats and risks:

Cyber Risk
Cybersecurity is critical in vendor assessments. Ransomware, distributed denial of service, and other attacks can shut down your organization, making it impossible for your company to fulfill its business obligations. While the 2020 SolarWinds Breach, in which attackers compromised SolarWinds’ Orion code base to install back doors, was perhaps the most significant cyber breach in recent years, it was by no means the only third-party breach.
- The personal data of millions of United Auto Workers retirees was stolen from Benefits administrator NationBenefits – including health plan ID, Medicare information, and Social Security numbers. Attackers exploited a cybersecurity weakness in the file transfer software used by NationBenefits to gain access.
- Customer proprietary network information (CPNI) on over 9 million AT&T wireless customers was stolen after attackers breached a marketing vendor for AT&T.
- An attack on Latitude Financial Services, a leading Australian personal loans provider, exposed personal information on over 330,000 customers of two of Latitude’s service providers. Exposed data included passports and passport numbers. Attackers breached a vendor to obtain Latitude employee login credentials.

Compliance Risk
Most organizations operate under a myriad of evolving regulatory requirements concerned with protecting sensitive data and systems. Many of these regulations, including HIPAA, the California Consumer Privacy Act (CCPA), the New York SHIELD Act, and Europe’s General Data Protection Regulation (GDPR), require organizations to protect the private information of their consumers, customers and employees. Other regulations concern the protection of non-public financial information. Violations can result in fines and reputational damage.

Financial Risk
Procurement teams must have visibility into the financial stability of their third-party vendors, including debts its vendors owe and the credit they extend to customers. A declaration of bankruptcy can result in lost business and supply chain disruptions.
ESG Risks
Investor concerns around environmental, social and governance (ESG) practices continue to grow. For example, following Russia’s invasion of Ukraine, doing business with firms affiliated with the Russian government became unpalatable to many companies. Organizations also need to protect themselves against accusations that their supply chain is involved with human rights violations, employing child labor, or causing environmental damage.
Reputational Risk
Adverse media coverage or negative news about a vendor has the potential to harm the reputation of its customers. This can happen when the vendor is involved in unethical hiring practices, quality issues with their products, criminal activities, or environmental disasters.
Navigating the Vendor Risk Lifecycle: Keys to Success
This complimentary guide details best practices for successfully managing risk throughout the vendor lifecycle. See what we've learned in our 15+ years of experience working with hundreds of customers.

Vendor Risk Management Challenges
Building an effective vendor risk management program can be a complex process that requires careful planning and execution. Here are nine challenges that your organization may face when building a VRM program:
Identifying third-party vendors
One of the primary challenges is identifying third-party vendors that your organization deals with, as these vendors may be spread across various departments and functions.
Assessing vendor risks
Once vendors are identified, assessing their risk can be complex and time-consuming, especially if your organization is using spreadsheets or other manual methods to gather and track responses.
Defining risk tolerance
To make more informed risk mitigation decisions, it's important to define your organization's risk tolerance levels, and establish thresholds for third-party risk exposure. A structured approach to vendor tiering and categorization is essential here.
Establishing due diligence procedures
Make sure you have robust vendor due diligence procedures in place. These should address a range of topics such as financial stability, compliance and cybersecurity.
Ensuring contract compliance
It's important to ensure that vendors are adhering to the terms of their contracts, especially with respect to security and compliance requirements.
Monitoring vendor performance
Be sure to monitor vendor performance and SLAs on an ongoing basis to ensure that service levels are met, and to identify any issues that may arise.
Keeping up with regulatory changes
Keeping up with changing regulatory requirements can be challenging, as vendor risk management is a key factor in many cybersecurity frameworks, industry guidelines, data privacy laws and ESG regulations.
Ensuring executive buy-in
Establishing an effective vendor risk management program requires executive buy-in and support, which can sometimes be challenging to obtain.
Aligning internal resources
Successful vendor risk management programs require collaboration between several different departments, including IT security, risk management, procurement, data privacy, legal and compliance.
8 Best Practices for a Successful Vendor Risk Management Program
Being in "reactive mode" is exhausting, inefficient and stressful – and it's especially risky when your workload gets heavy. Vendor risk management (VRM) is no different: Having a reactive VRM program that responds to vendor risk, instead of proactively managing vendor risk, puts your organization in jeopardy of data breaches, privacy violations and regulatory compliance infractions.
That’s why it's important to have a clear process for proactively managing the third-party cyber risks and business continuity exposures that inevitably crop up throughout the vendor relationship lifecycle.
In our 15+ years working with thousands of customers and vendors, we've developed 8 best practices for building a more proactive vendor risk management (VRM) program.
Here's a sneak peek at some of these practices and how they can take the pain out of vendor risk management:

1. Onboard, Score and Manage Vendor Risks
You need to make several decisions prior to kicking off a vendor risk management program. Expert advisory services can help define the parameters of the program. The next step is to get control of your third-party vendors, onboard them, and identify their inherent risks.
Key decisions at this step include:
- What is the right mechanism for onboarding vendors? Will you use a manual process or spreadsheet template? Will you require integrations with procurement or vendor management systems?
- Which factors will you consider in making vendor tiering decisions? For instance, which attributes or criticality concerns will impact how you tier specific vendors?
- How will you collect information to assess inherent risk? Will you use an automated questionnaire? What inputs will be used to calculate inherent risk (e.g., operational, legal, regulatory, financial, and/or reputational data)?
When you first engage potential VRM solution providers, make sure they offer multiple mechanisms for onboarding vendors, suppliers and other third parties. This may include performing onboarding tasks on behalf of your team.
Also, ensure that their vendor tiering and vendor risk scoring methodology includes more than just surface-level questions. For instance, you may want it to include financial and supply chain considerations as well. Read our best practices guide for a full accounting of these attributes.
2. Automate Key Aspects of the VRM Process
The next step to proactive vendor risk management is to stop using spreadsheets for vendor risk assessments. Of course, you still need a way to collect evidence of security controls and perform due diligence reviews per your corporate standards and compliance requirements. Fortunately, you can automate this process and eliminate the redundant, soul-crushing assessment tasks that often lead to errors and risks.
Collection and due diligence review can take many forms. For instance, you can manage the assessment process yourself; access a library of completed questionnaires; or outsource collection to a partner. In fact, we see many companies successfully managing risks with a hybrid model that taps different approaches for different tiers of vendors.
Key decisions at this step include:
- Which questionnaire will be used to gather information about your vendor’s controls? Will you use industry-standard or proprietary surveys? (Hint: It depends on a combination of two things: 1) Which regulations or frameworks you plan on mapping the answers to, and 2) Whether you plan to share the results with a network.)
- Which collection method(s) will you use? Do you have the resources and expertise to manage this in-house? Will you take advantage of networks of completed vendor responses to speed up the process? Will you outsource collection to a partner? (Ideal for under-resourced teams or those without the bench strength.)
As with Step 1, make sure your VRM solution provider is flexible in terms of questionnaire availability and collection methods. You probably don’t want to be locked into a single rigid questionnaire that can't be customized. You also don't want to be forced to collect due diligence on your own, especially if you're short-staffed.
3. Make Smarter Decisions with Continuous Vendor Risk Intelligence
The next step in building your vendor risk management framework is to validate third-party assessments with external cybersecurity and business risk intelligence. While periodic assessments are essential to understanding how vendors govern their information security and data privacy programs at a given point in time, a lot can happen to a vendor between assessments! This is where continuous monitoring can help.
Many organizations fall short here. Too many take a narrow, qualitative view of vendor risks and ignore more qualitative information. When combined and correlated, cybersecurity and business monitoring provide a more comprehensive view of vendor risk. This "outside-in” view gives you an edge in grasping the potential impact of vendor risk. It also augments your “inside-out” assessments to deliver a more informed and accurate risk score. But what types of monitoring information should you focus on?
- Cybersecurity risk intelligence sources: Understanding weaknesses that are visible to attackers starts with uncovering compromised data on the dark web and cataloging security breach disclosures. It continues with gathering information on validated cyber-attacks, infrastructure and IT policy violations, vulnerabilities and other exposures.
- Business risk intelligence sources: Insights on risks posed by operational issues, M&A activity, layoffs, leadership changes, product recalls, regulatory/legal probes, financial and bankruptcy notifications are all important qualitative inputs that add further context to the VRM process.
Read the best practices guide for a deeper dive into each of these intelligence sources.
With the right intelligence, you can help vendors clean up their open-source footprints and close security gaps in their internal processes. The process is similar to polishing your credit report prior to applying for a home loan.
Vendor Risk Assessment: The Definitive Guide
Download this 18-page guide to gain comprehensive guidance on how to conduct and implement vendor risk assessments at your organization.

4. Fix What’s Important with Recommended Remediations and Reporting
Now comes the hard part: remediating the risks! Key considerations at this stage include:
Does your team have the expertise to recommend remediations for failed controls? Would it be helpful to automatically trigger pre-defined remediations when assessments flag specific risks?
How do you plan to project future risk (e.g., residual risk) over time after the application or enforcement of remediations? This will be important in board-level reporting.
How will you demonstrate a vendor’s compliance with a specific regulatory or industry framework? (Hint: Look for solutions that provide "percent-compliant" metrics against multiple regulations.)
How will you mitigate hidden threats that aren't revealed by assessment responses? (Be sure to ask if your VRM solution includes machine learning to analyze data and reveal hidden trends.)
5. Take a Continuous, Intelligent and Automated Approach to Vendor Risk Management
The final step in moving toward more proactive VRM is to incorporate continuous and intelligent automation into your program over the long term. This includes taking advantage of solutions that can proactively and continuously assess, monitor and eliminate vendor risk. But what does "continuous, intelligent and automated" look like?
Continuous assessments
One way to achieve a more continuous, less reactive assessment model is to enable real-time cyber and business monitoring intelligence to inform your assessment schedule. With the right rules in place, you can correlate a vendor’s vulnerabilities, breaches or leaked credentials on the dark web with assessment responses revealing weak password management or patch management practices. You can then use these findings to trigger assessments. This level of automation truly closes the loop on third-party risk and transforms point-in-time assessments into continuous vendor risk monitoring.
Intelligence from every corner
Making sound, risk-based decisions means consuming and normalizing data from several sources. See our best practices guide for a diagram illustrating the inputs typically required to inform risk-based decision-making. Here are just a few:
Public and private sources, vendor risk intelligence and technology integrations can provide quantitative and qualitative insights into IT security risks, financial problems and other indicators of a vendor's cyber and business health.
The vendor community, completed assessments and industry partnerships also play a part. They provide member-supplied or crowd-sourced documentation and insights that can provide a preview into what risks vendors pose in specific industries.
Regulatory monitoring provides insights into control failures across regulated industries and can help anticipate the remediations required to reduce a vendor's residual risk.
Automation playbooks to streamline risk response
One way to achieve a more automated program is to leverage capabilities for triggering risk response actions based on “If This, Then That” criteria for specific entities and risks. Rules should automate a broad range of onboarding, assessment and review tasks. These can include updating vendor profiles and risk attributes, sending notifications, and/or activating workflows. They should also run perpetually to update the VRM environment as new events and risks emerge.
6. Account for Geopolitics in Your VRM Plan
The increasingly fraught geopolitical situation also can pose substantial risks to vendor risk management programs. Evaluate your vendors based on where they do business. Vendors with a heavy business concentration in countries with poor track records on human rights and ESG may be putting themselves and their services to your organization at risk. Sudden tariffs or an embargo could dramatically reduce revenue and lead to vendor performance risk or even failure.
On the same token, organizations that do substantial business or host data in countries without explicit laws regarding data privacy may put your organization's data at risk through mandated sharing with government entities in the host country. Here are some questions worth asking about current vendors as well as future potential vendors during your sourcing and selection process:
Does the vendor have substantial business operations or host data in countries without clear laws and regulations pertaining to how data is shared between government and private sector entities?
Does the vendor operate in countries with poor track records on human rights, political freedom, or environmental degradation? If so, are their operations substantial enough to cause disruption if that country was to be embargoed?
Does the vendor base their operations in a country with disputed territory or active violent insurgency?
eBook: 25 KPIs and KRIs for Third-Party Risk Management
The 25 Most Important KPIs and KRIs for Third-Party Risk Management will put you on the path to more effective communication regarding your TPRM program.

7. Build in Compliance Reporting from the Ground Up
Since third-party risk management is a key control focus in most regulatory regimes and industry frameworks, it’s important to show progress toward achieving compliance with those requirements – for auditors both outside and inside your organization. However, many risk management tools make compliance reporting overly complex and time-consuming. Built-in reporting for common regulations and industry frameworks is therefore key to speeding and simplifying the compliance process.
One way to speed compliance reporting is to gain visibility into each vendor’s level of compliance. Start by establishing a compliance “pass” percentage threshold against a risk category (e.g., X% compliant against a particular framework or guideline). All reporting will tie back to that percent-compliant rating, and your team can focus on areas where compliance pass rates are low. This should also be conducted at the macro level across all vendors; not just at the vendor level. Macro-level reporting will be important for the board as they seek to determine how compliant the organization is against the “flavor of the month” regulation.
Bonus Tip: Vendor ESG Compliance Is Becoming Increasingly Important
ESG regulations from the California Supply Chain Transparency Act to the EU Draft Directive are placing increasing pressure on companies to eradicate poor ESG practices from their supply chains, a trend that looks set to continue throughout the 2020s. While many organizations see ESG as primarily a concern for suppliers, IT vendors can also pose ESG risks ranging from poor labor practices at factories to bribery and other forms of corruption. Take a careful look at ESG Compliance requirements that may affect your organization and ensure that you structure compliance reporting to account for them.
8. Ensure Vendor Offboarding Is Smooth, Efficient and Verified
When a vendor relationship ends, risk can persist. A vendor holding sensitive data must return and/or securely destroy that data; support obligations may outlive a purchase agreement; and organizations must ensure that any third-party access to internal systems is terminated. While this is easily understood, Prevalent research found that 60 percent of companies are not actively assessing third-party risks during offboarding. This presents ongoing business, security, and IP risk.
Here are a few key questions to ask about your current vendor offboarding approach.
Do we have verification methods in place to ensure that offboarded vendors are terminated from access to all IT infrastructure and applications?
Do we routinely audit systems to verify that vendors have been successfully offboarded?
Does our vendor offboarding approach incorporate key provisions of applicable compliance requirements?
Do we require vendors to affirm in writing that all sensitive data has been destroyed upon the completion of offboarding?
Do we write offboarding requirements into contracts and SLAs with vendors?
Next Steps: Download the Vendor Risk Management Best Practices Guide
Now that you have an idea of what an enterprise vendor risk management deployment looks like, be sure to uncover more details in best practices guide.
Prevalent delivers a complete vendor risk management solution that's unified by a single, easy-to-use platform. If you would like to learn more about how to construct your complete VRM strategy, request a demo today
-

The Third-Party Vendor Risk Management Lifecycle: The Definitive Guide
Your organization encounters distinct risks at each step of the vendor relationship, making it important to...
03/07/2024
-

Understanding Inherent Risk vs. Residual Risk
Examine the similarities and differences between inherent risk and residual risk, a learn how they provide...
01/25/2024
-

Data Privacy and TPRM: 5 Best Practices
Learn how to navigate the complexities of safeguarding PII, PHI and other sensitive data in the...
01/09/2024
-
Ready for a demo?
- Schedule a free personalized solution demonstration to see if Prevalent is a fit for you.
- Request a Demo




